Information Security
Udacity Quizzes
18 minute read
Notice a tyop typo? Please submit an issue or open a PR.
Udacity Quizzes
The Security Mindset
Security Impact Quiz

Security Impact Quiz Solution
No one right solution. I think the important thing to understand here is that no company is safe from a breach, and many companies that you interact on a daily basis have suffered breaches.
Black Market Prices Quiz

Black Market Prices Quiz Solution

I think the point here is not to remember the exact numbers, but rather to understand that this information can be purchased relatively cheaply. This makes sense given that millions of records can be retrieved in a single breach.
Sony Pictures Quiz
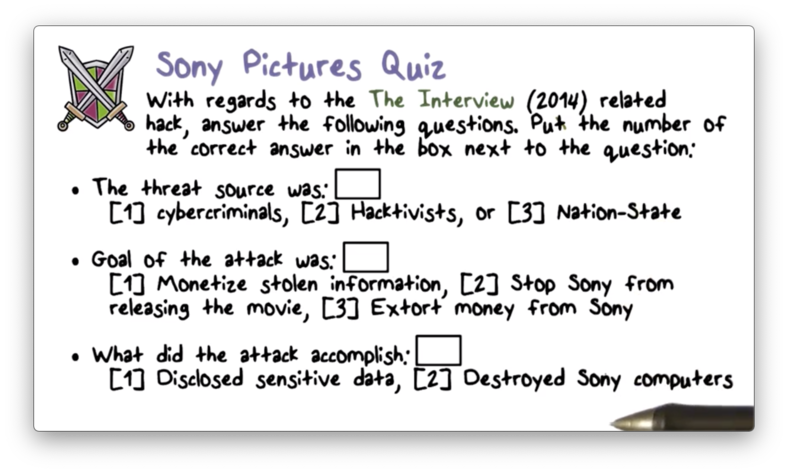
Sony Pictures Quiz Solution
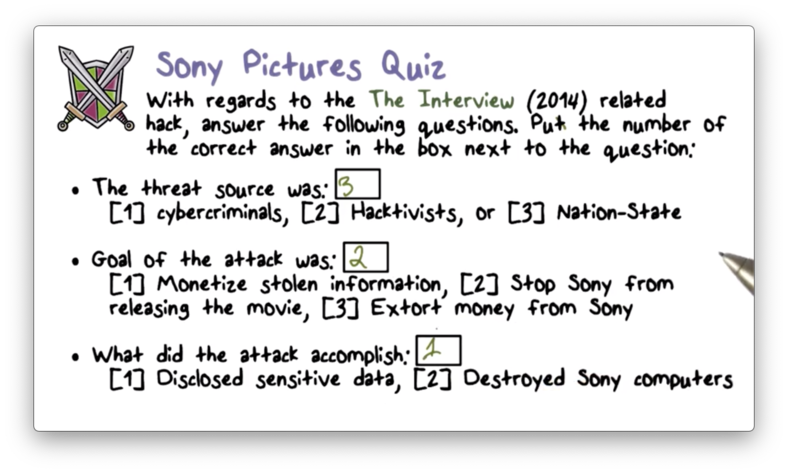
Read more here
Security Requirements Quiz

Security Requirements Quiz Solution

Since data breaches involve the disclosure of information to unauthorized parties, these breaches violate confidentiality.
Losses Due to Cyber Crime Quiz

Losses Due to Cyber Crime Quiz Solution

Security Mindset Quiz

Security Mindset Quiz Solution

Software Security
Stack Access Quiz
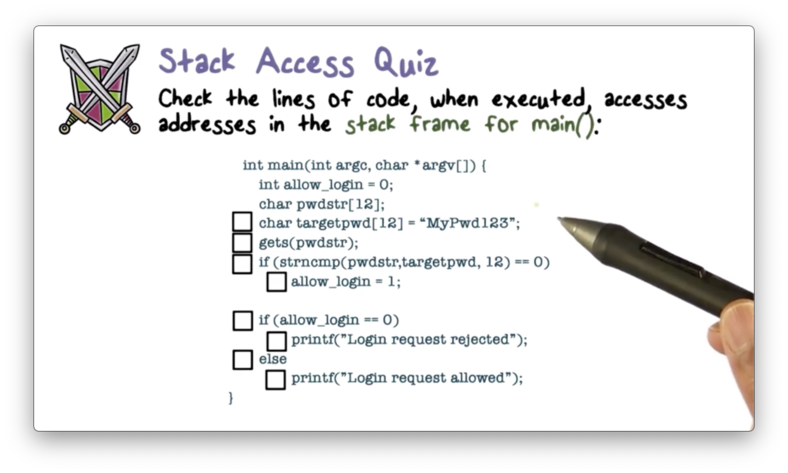
Stack Access Quiz Solution

Since allow_login, pwdstr and targetpwd are all local variables to main, any access of them will access memory locations inside the stack frame for main.
The only lines of code that don't access the stack frame for main are the calls to printf, (which create a new stack frame), and else.
Attacker Code Quiz

Attacker Code Quiz Solution

Remember that the stack pointer moves down in memory as space is allocated. This means that allow_login will receive memory starting at the highest feasible address, and pwdstr will receive memory starting at the next highest feasible address.
Suppose both int and char occupy 1 byte. allow_login may be allocated 1 byte of space starting at memory address 1000. pwdstr may be allocated 12 bytes of space starting at memory address 988.
If the user enters a password longer than 12 bytes, the remaining bytes will overflow into the memory allocated to allow_login, effectively overwriting its value.
Since login will succeed if allow_login is anything but 0 (i.e. not a fail-safe default), this overflow will almost certainly lead to access being granted.
Buffer Overflow Quiz

Buffer Overflow Quiz Solution
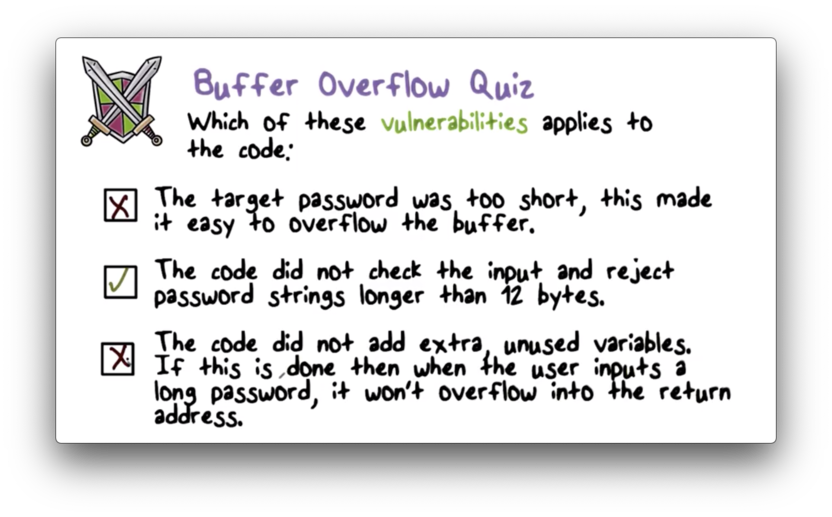
The first answer is wrong. The target password can be as long as you'd like, but if the attacker submits a longer password, the overflow will still happen.
The third answer is also wrong. Besides the fact that you shouldn't ever really add useless variables, these variables will only provide a finite amount of distance between the user-filled buffer and the return address. With a long enough password, the attacker can still overwrite the return address.
Only the second answer is correct. The overflow happens precisely because input larger than the space allocated for that input is not rejected by the program.
NVD Quiz
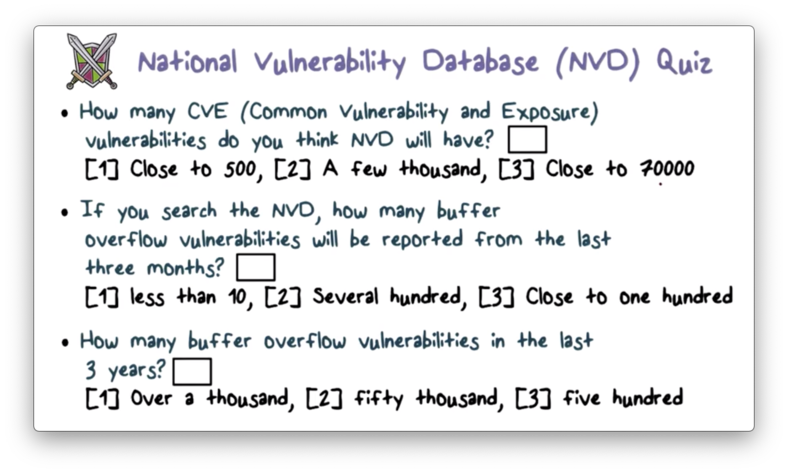
NVD Quiz Solution

Strongly Vs Weakly Typed Language Quiz

Strongly Vs Weakly Typed Language Quiz Solution

Buffer Overflow Attacks Quiz

Buffer Overflow Attacks Quiz Solution

Stack canaries do prevent return-to-libc buffer overflow attacks, because stack canaries prevent return address overwriting. Without overwriting the return address, a function can only return to the function that called it.
ASLR does not protect against read-only buffer overflow exploits. ASLR only makes it harder to supply key addresses in write-based buffer overflow exploits.
Heartbleed cannot be avoided by using a non-executable stack. Heartbleed is a read-based buffer overflow exploit, and the attack did not involve injecting any machine instructions onto the stack.
Operating System Security
Secure OS Quiz 1

Secure OS Quiz 1 Solution

Secure OS Quiz 2

Secure OS Quiz 2 Solution

A system call requires control transfer from the calling process into the OS, which then must perform authentication/authorization checks before granting access and transferring control back.
This is more costly than a regular call, which incurs none of this overhead.
Secure OS Quiz 3

Secure OS Quiz 3 Solution
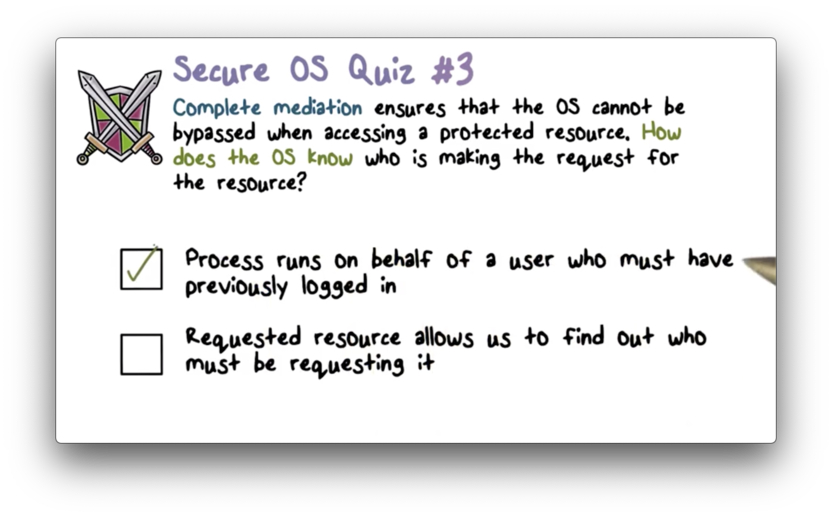
Processes run on behalf of users. Users must login to the system to run applications/processes.
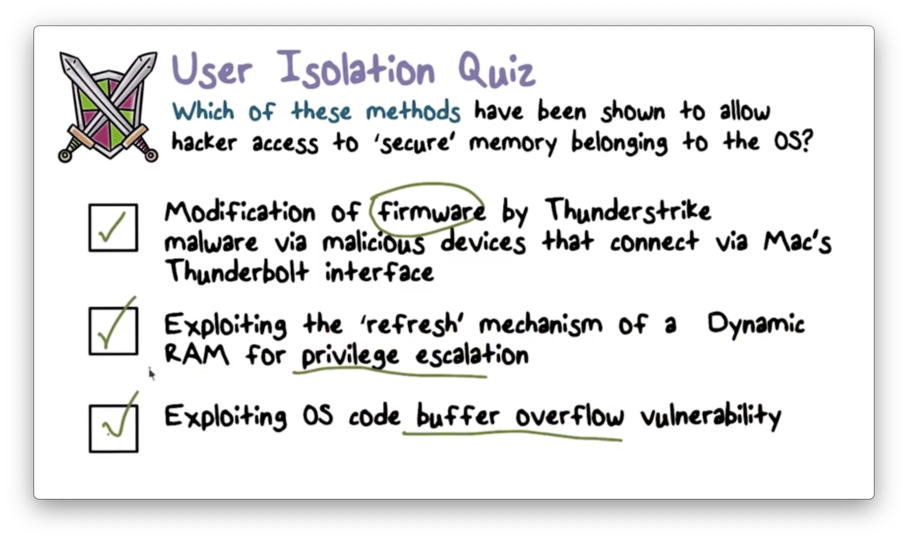
User Isolation Quiz
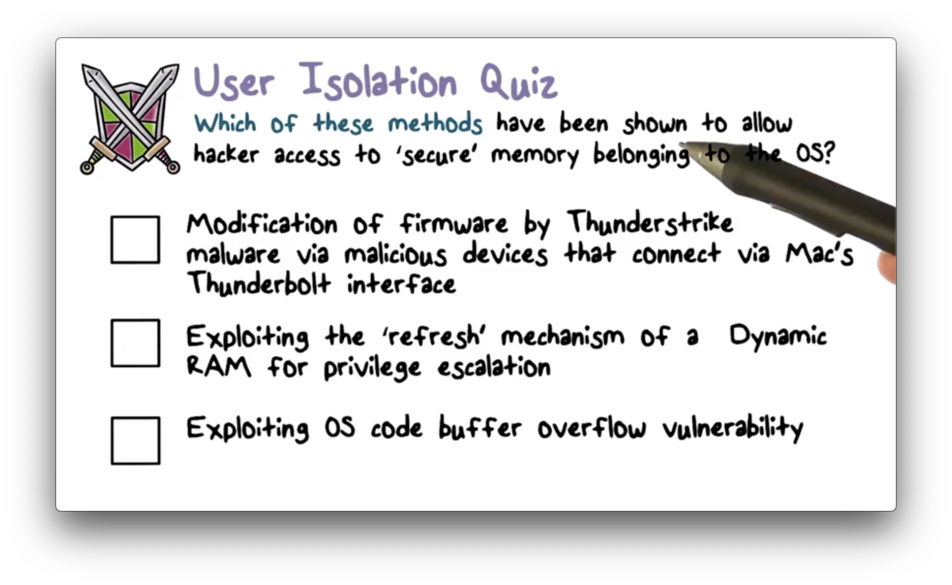
User Isolation Quiz Solution
Revisiting Stack Overflow Quiz

Revisiting Stack Overflow Quiz Solution

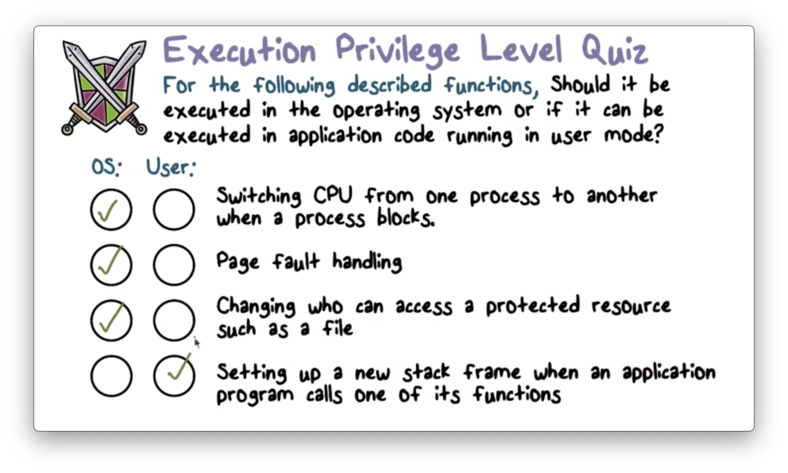
Execution Privilege Level Quiz
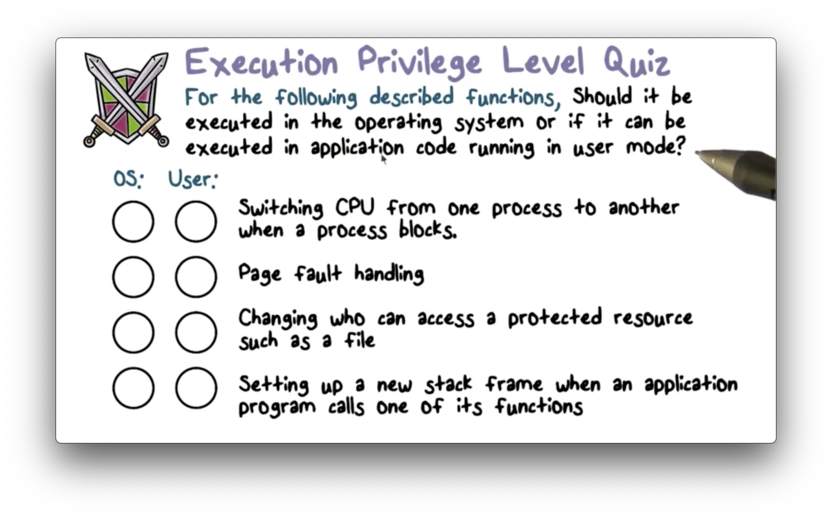
Execution Privilege Level Quiz Solution
TCB Requirements Quiz
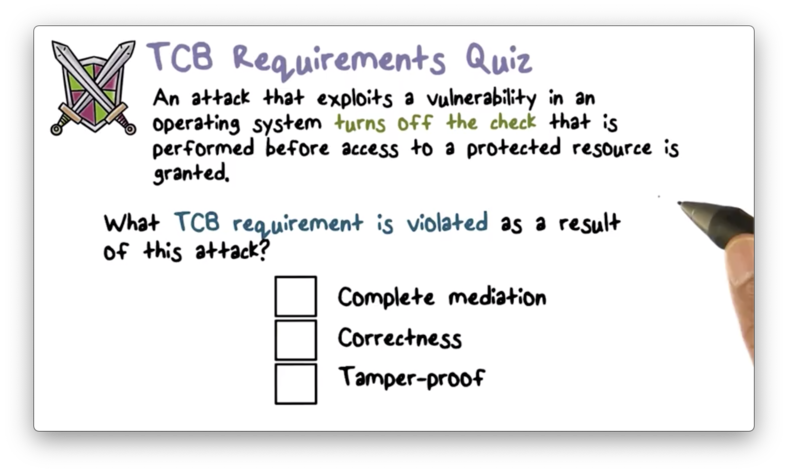
TCB Requirements Quiz Solution

In this case, we have tampered with the TCB by turning off the check. The access still proceeds through the operating system, and is still technically correct (i.e. the access wasn't permitted because of a bug).
Size of Security Code

Size of Security Code Solution

I think the point being made here is that the increase in complexity may be accompanied by an increase in vulnerability.
Hypervisor Code Size Quiz

Hypervisor Code Size Quiz Solution

Again, the argument being made here is that using a hypervisor as a TCB, with fewer lines of code than a full-fledged operating system, might be a more secure choice.
Authentication
Authentication Quiz

Authentication Quiz Solution

If someone steals your phone, you will be thankful for your lock screen/passcode.
Login Attacks Quiz
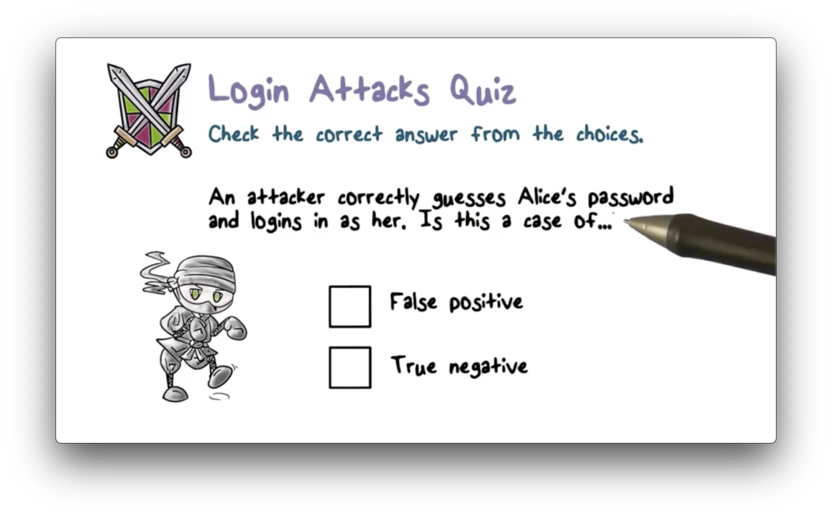
Login Attacks Quiz Solution
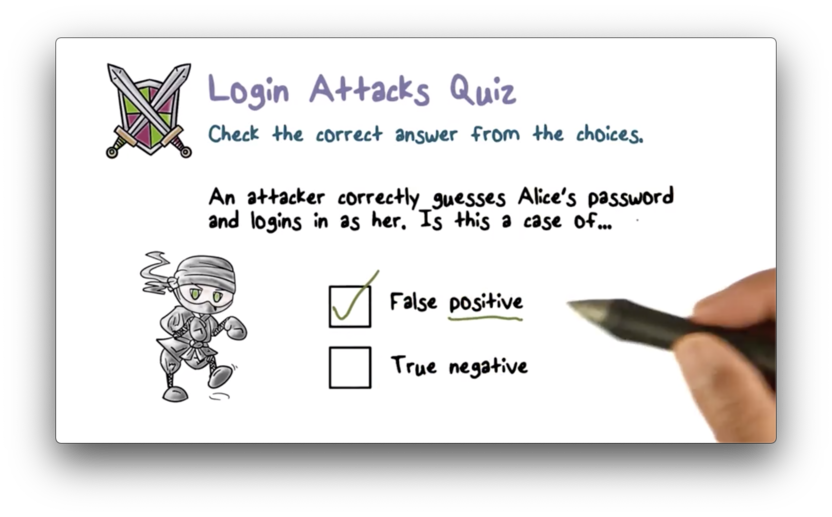
Remember, the positive event is gaining access to the system. A false positive is gaining access erroneously. An attacker authenticating as someone else is a false positive.
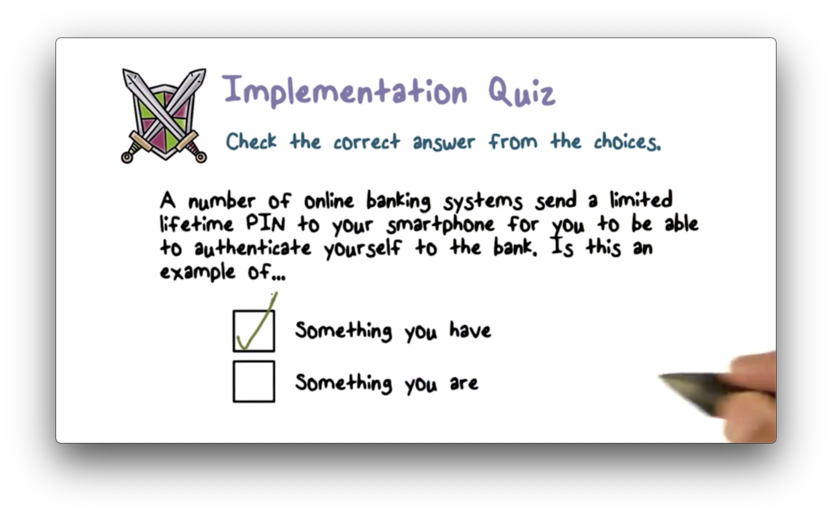
Implementation Quiz

Implementation Quiz Solution
Password Popularity Quiz

Password Popularity Quiz Solution

If we are attacking systems, we might get the best bang for our buck trying these passwords.
Password Quiz

Password Quiz Solution
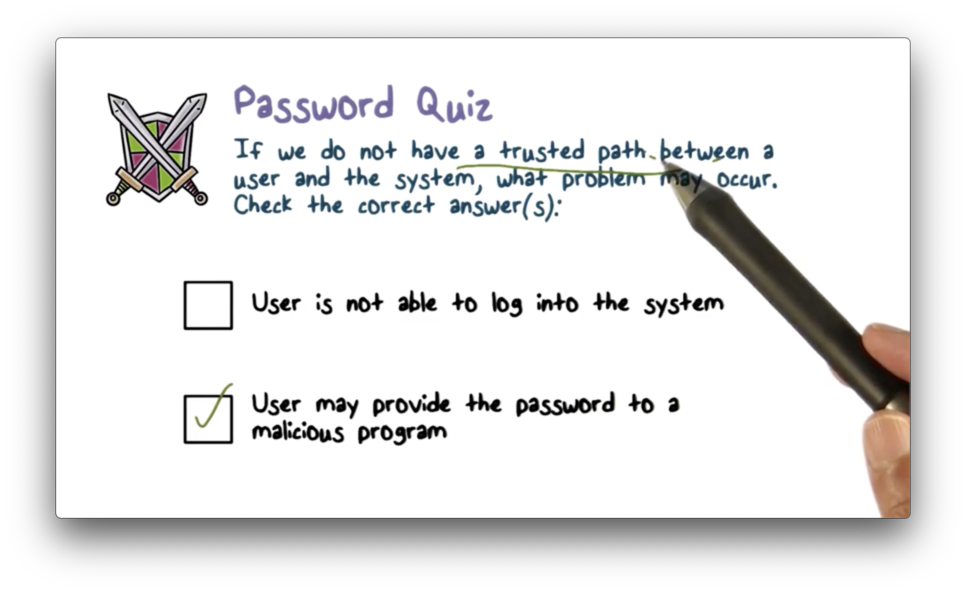
A trusted path ensures that there is no application between the user and the operating system. Without this path, malicious programs may intercept login credentials.
Hashed Passwords Quiz

Hashed Passwords Quiz Solution

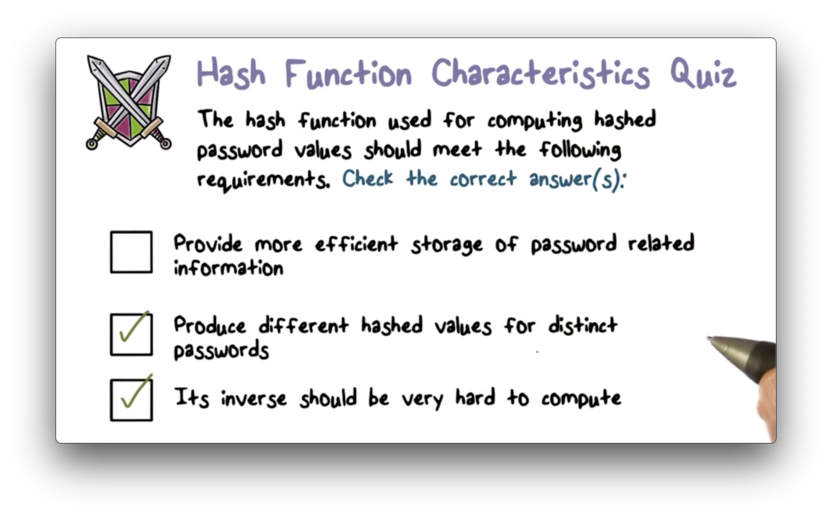
Hash Function Characteristics Quiz
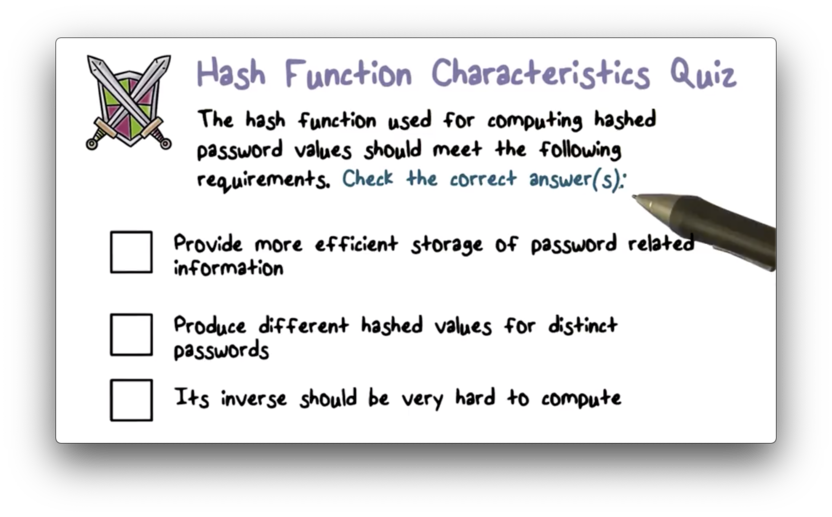
Hash Function Characteristics Quiz Solution
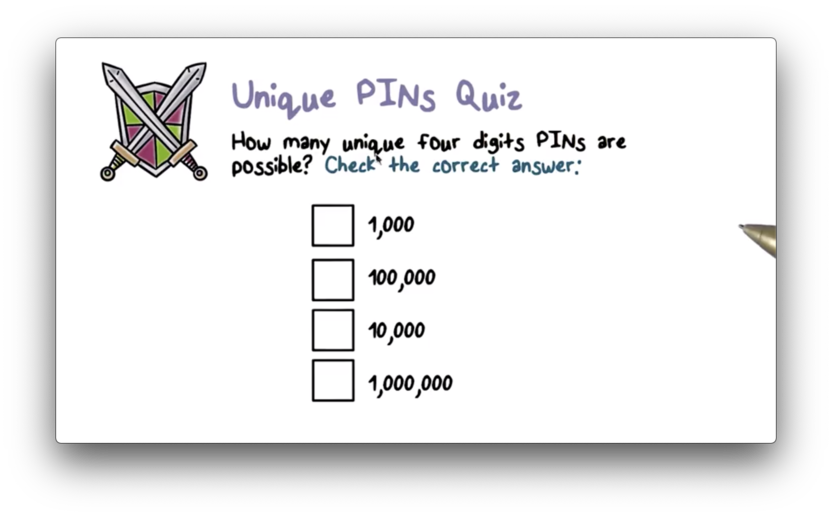
Unique PINS Quiz
Unique PINS Quiz Solution
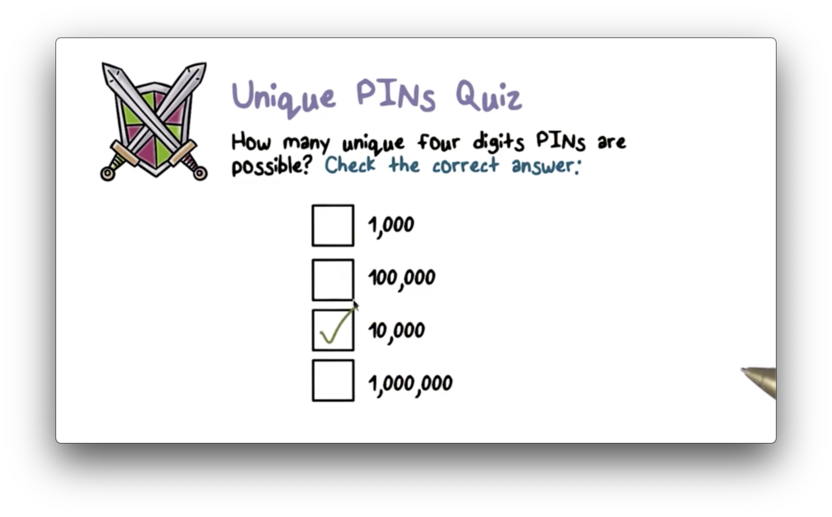
With ten options for the first digit, ten options for the second digit, and so on, the total number of four digit pins is 10 10 10 * 10, or 10^4, or 10,000.
Brute Force Quiz

Brute Force Quiz Solution

With 72 options for each other six characters, the total number of unique passwords is 72^6, which is the number of attempts the hacker will have to make in the very worst case.
Touch Screen Passwords Quiz
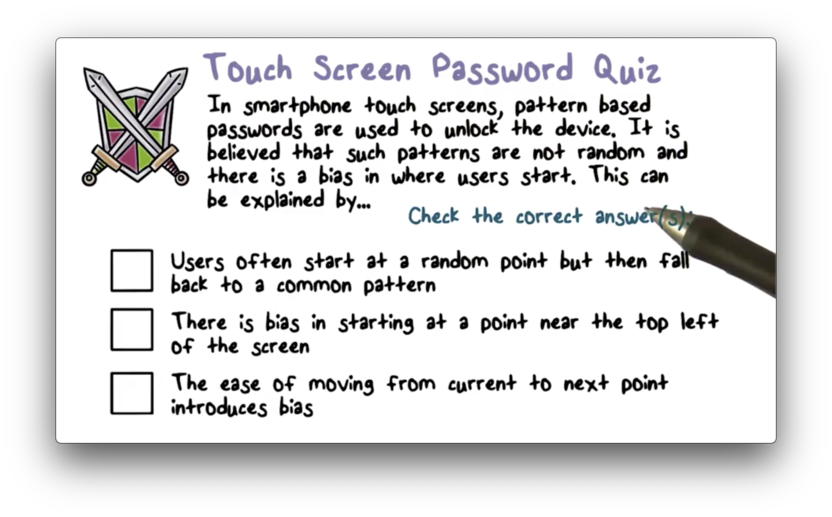
Touch Screen Passwords Quiz Solution
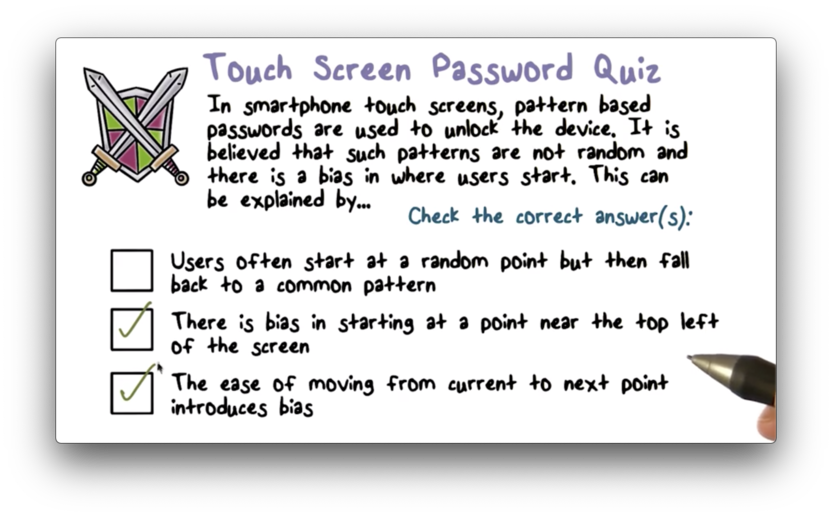
Basically, the idea here is that attackers will likely not have to exhaustively search the space of possible patterns because biases exist that greatly shrink this space into a much smaller space of much more probable patterns.
Multi-factor Authentication Quiz

Multi-factor Authentication Quiz Solution

Remember, a false positive occurs when a malicious user is granted access to the system as a valid user. The likelihood of this happening decreases when multiple authentication components are employed by the system.
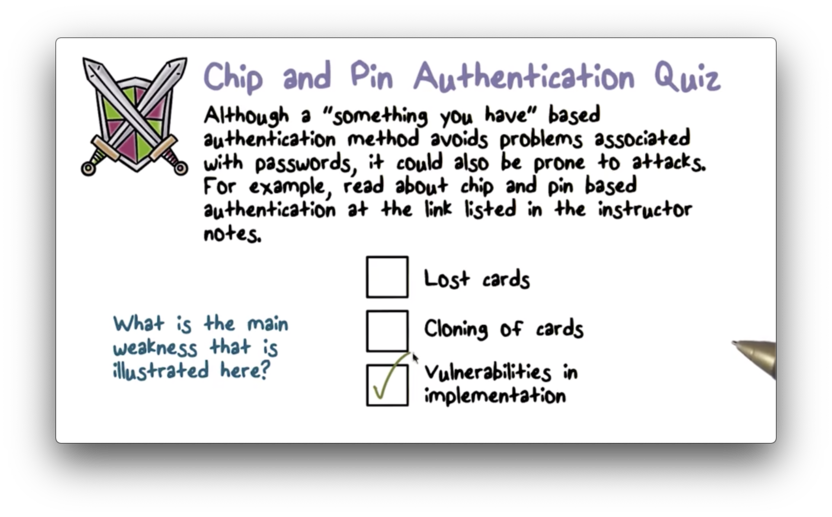
Chip and Pin Authentication Quiz
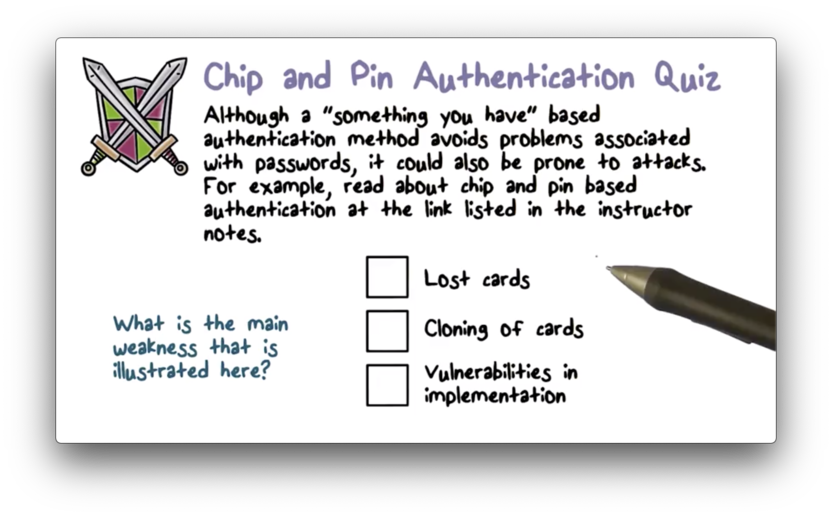
Chip and Pin Authentication Quiz Solution
Biometric Authentication Quiz
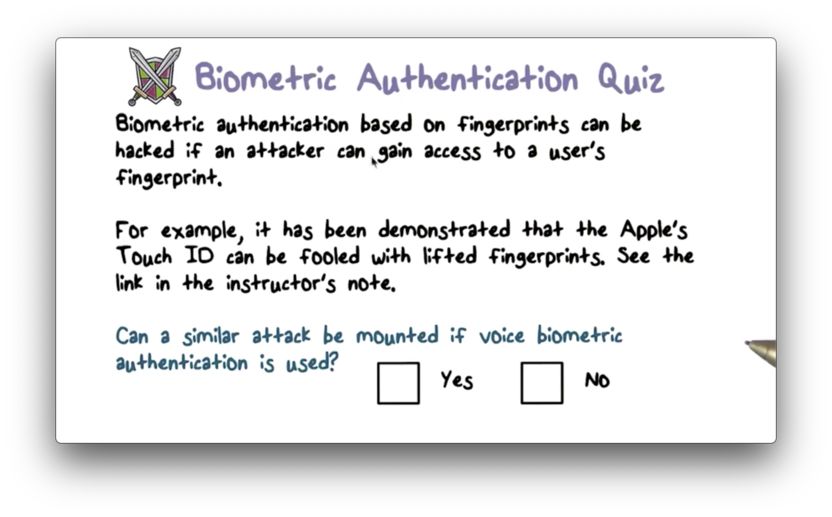
Biometric Authentication Quiz Solution
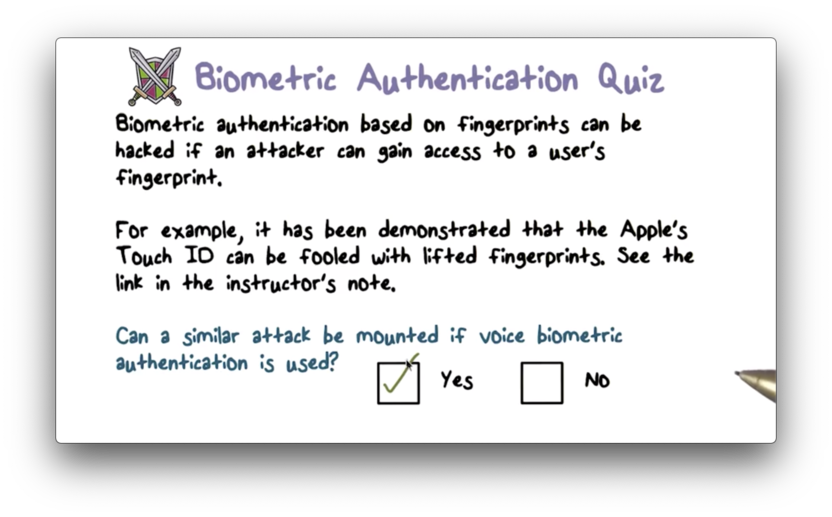
As a basic example, consider someone recording your voice and playing it back to a voice-based authentication system.
Access Control
Data Confidentiality Quiz

Data Confidentiality Quiz Solution

Controlling read access is connected to data confidentiality, while controlling write access is connected to data integrity.
Determining Access Quiz

Determining Access Quiz Solution

Access control conflicts can be securely resolved by denying access.
Discretionary Access Control Quiz

Discretionary Access Control Quiz Solution
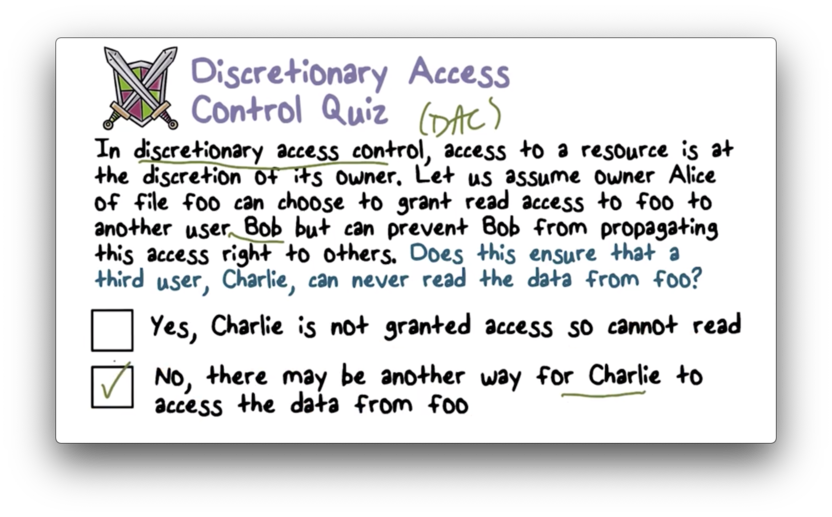
Bob can write the contents of the file to a new file that he owns, and share that file with Charlie.
ACE Quiz
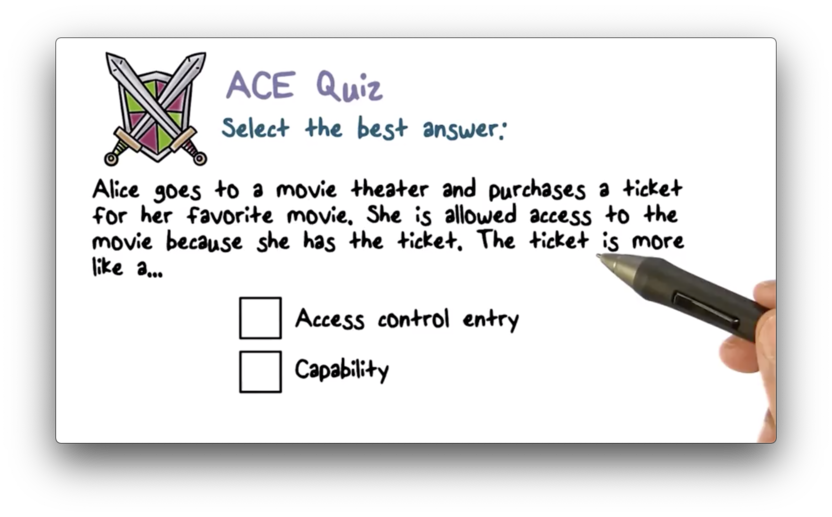
ACE Quiz Solution
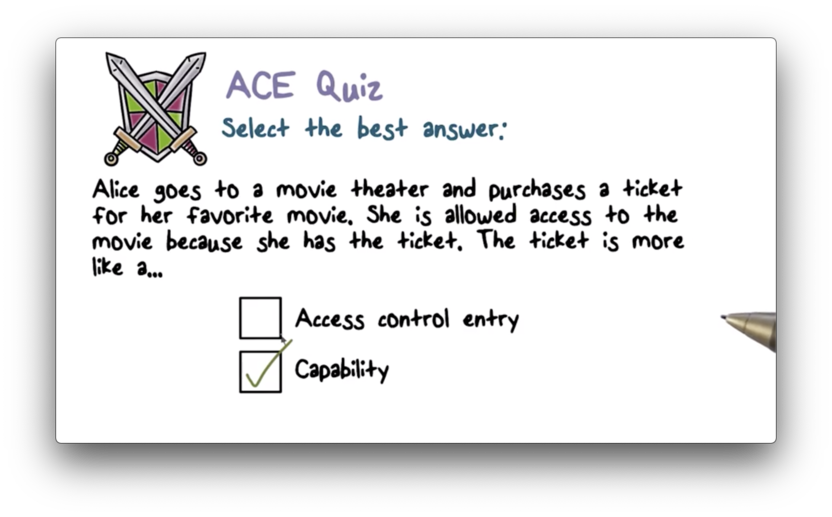
The presentation of the ticket is sufficient to gain access to the theater. No other access checks are required. This is closest in functionality to a capability.
ACE Access Quiz

ACE Access Quiz Solution

Negative access rights supersede positive access rights, so you can't terminate as soon as you find a positive access right. You can terminate as soon as you find a negative access right, though.
NB: The third option can't be true if the second option is true.
Revocation of Rights Quiz
Revocation of Rights Quiz Solution
Time to Check vs Time to Use Quiz

Time to Check vs Time to Use Quiz Solution

As long as you had the permissions when you called open, you can access the file using the file descriptor.
Unix File Sharing Quiz
Unix File Sharing Quiz Solution
You would need to somehow add the descriptor to the per-process descriptor table for the process with which you wish to share the descriptor. Since the OS owns this table, mutating it is impossible.
SetUID Bit Quiz

SetUID Bit Quiz Solution
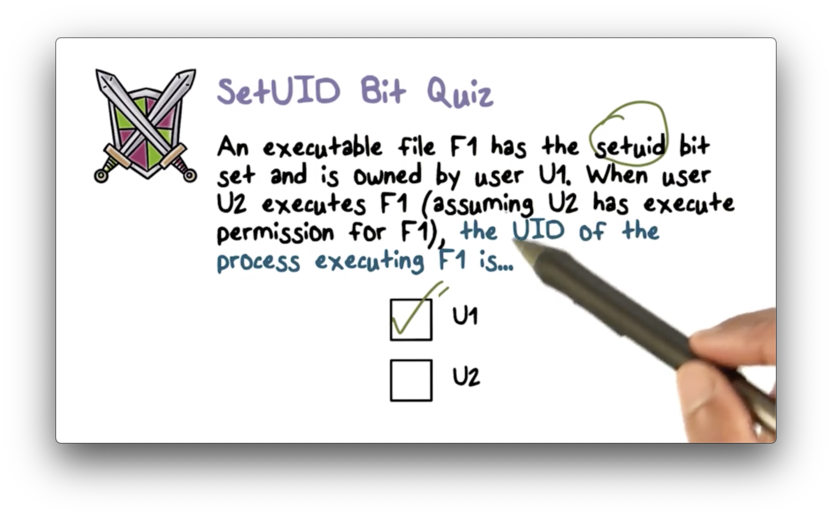
The effective UID of a process executing a file with the setuid bit set is the owner of the file, not the user who created the process.
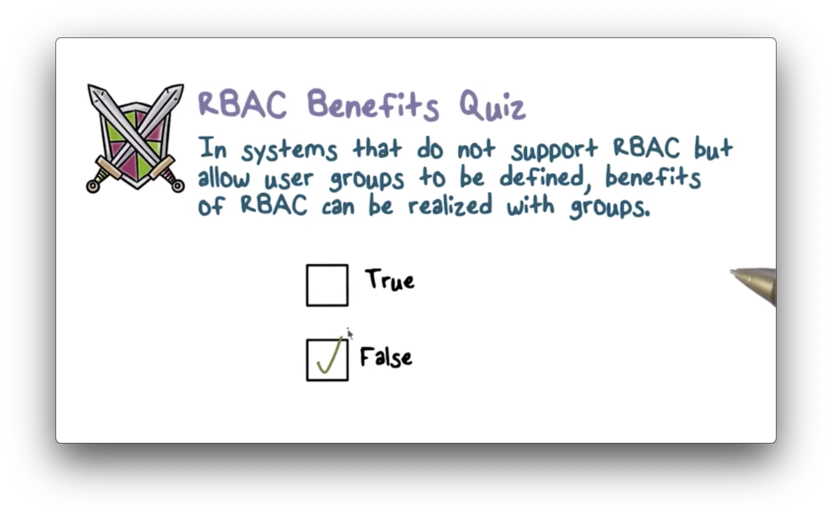
RBAC Benefits Quiz

RBAC Benefits Quiz Solution
Access Control Policy Quiz
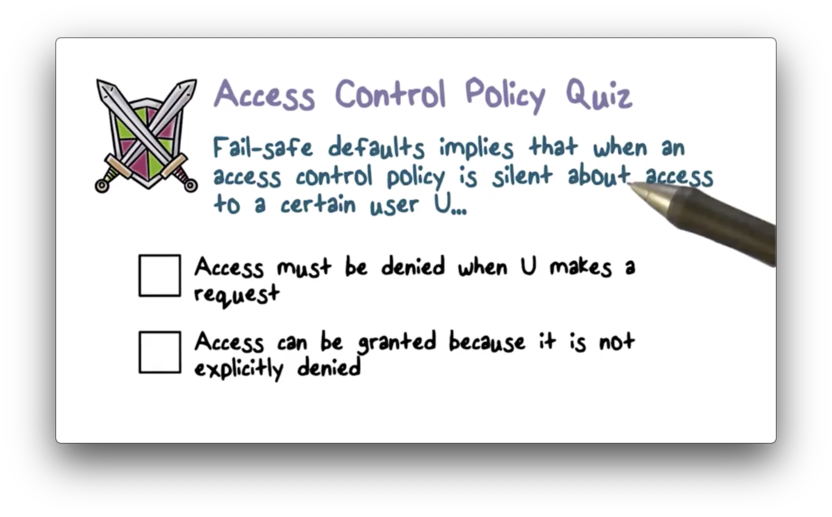
Access Control Policy Quiz Solution

From a security standpoint, denying access is a fail-safe default. It never fails to keep your system secure.
Mandatory Access Control
DAC Quiz
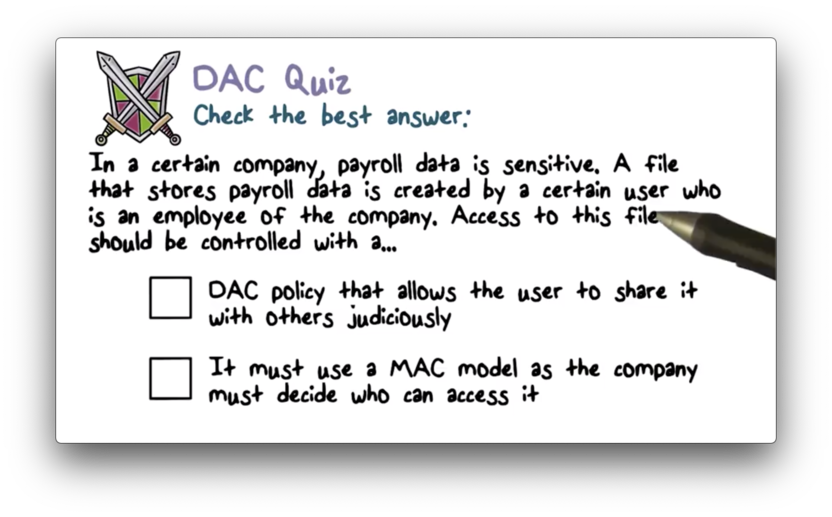
DAC Quiz Solution
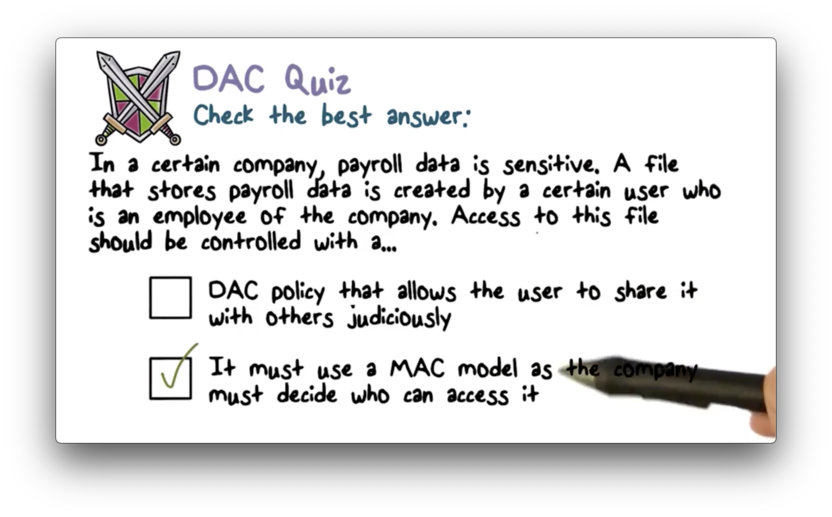
DAC can't control information flow, so we must use MAC.
Health Data Quiz

Health Data Quiz Solution

BLP is concerned with military/governmental intelligence. HIPAA is concerned with health information.
Security Clearance Quiz

Security Clearance Quiz Solution

Source: Washington Post
Order Quiz

Order Quiz Solution

Given any two real numbers, one number is always greater than the other.
Label Domination Quiz

Label Domination Quiz Solution
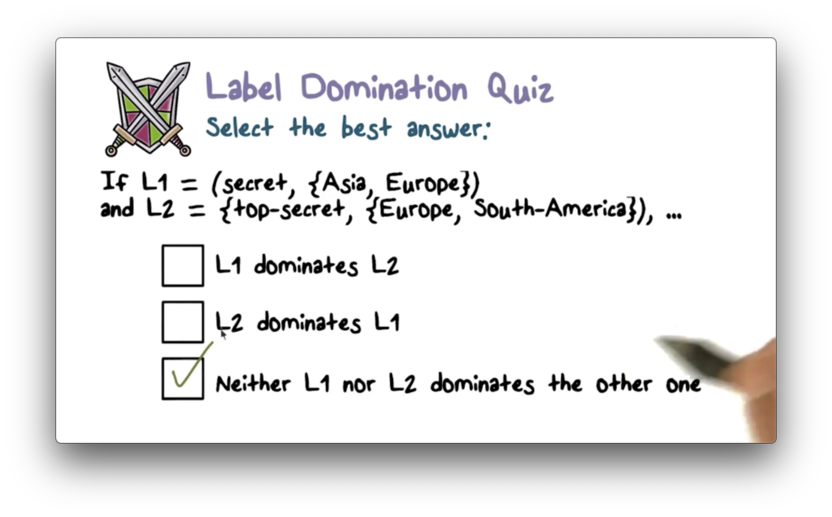
While secret < top-secret , {Asia, Europe} cannot be compared with {Europe, South-America}.
Sensitive Data Quiz

Sensitive Data Quiz Solution

In order for D1 to dominate D2, D1 must have a higher sensitivity level than D2.
In addition, the compartment of D1 must contain the compartment of D2 in order to be 'greater' (based on the ordering rules for sets). For this to be the case, the compartment of D2 must be a subset of ("narrower" than) the compartment of D1.
Unclassified Documents Quiz

Unclassified Documents Quiz Solution

Write-down says that individuals cannot write documents with a classification that is less than their security clearance. Therefore, unclassified documents cannot be written by individuals holding a security clearance of classified, secret, or top secret.
Classified Data Quiz

Classified Data Quiz Solution

Because of the write-up rule, individuals are allowed to write documents at a classification level that is greater than their clearance level. Individuals with unclassified security clearance are thus allowed to write top secret documents.
BLP Model Quiz
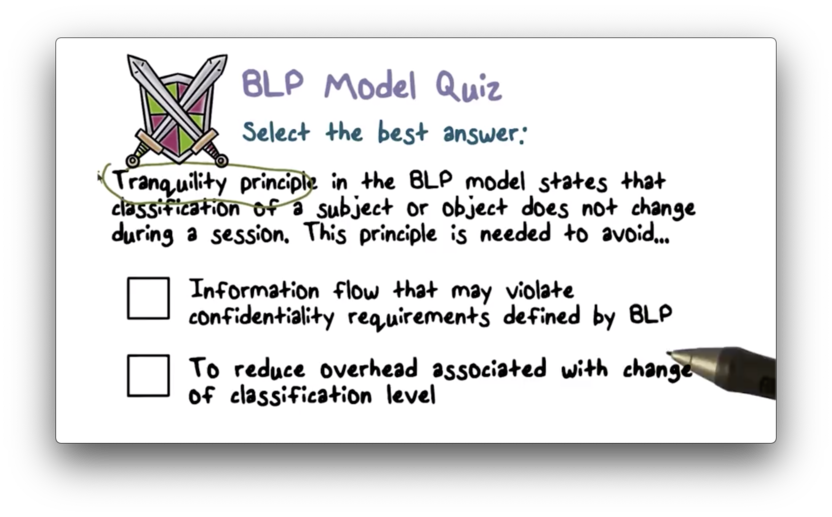
BLP Model Quiz Solution
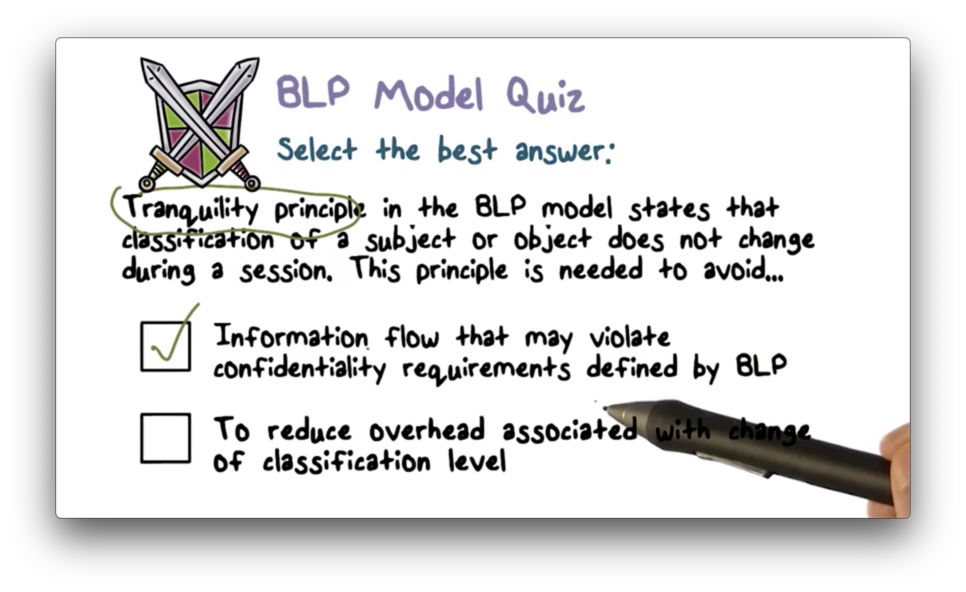
For example, if a user is writing to a top secret document, and the classification level suddenly changes to secret, the write-up rule is violated and information is flowing in the wrong direction.
Clark Wilson Quiz

Clark Wilson Quiz Solution

In mandatory access control, sharing decisions are not made at the discretion of the user.
COI Quiz

COI Quiz Solution

Competition implies that there is a possibility for a conflict of interest. Chinese Wall is best at preventing these situations.
RBAC Quiz
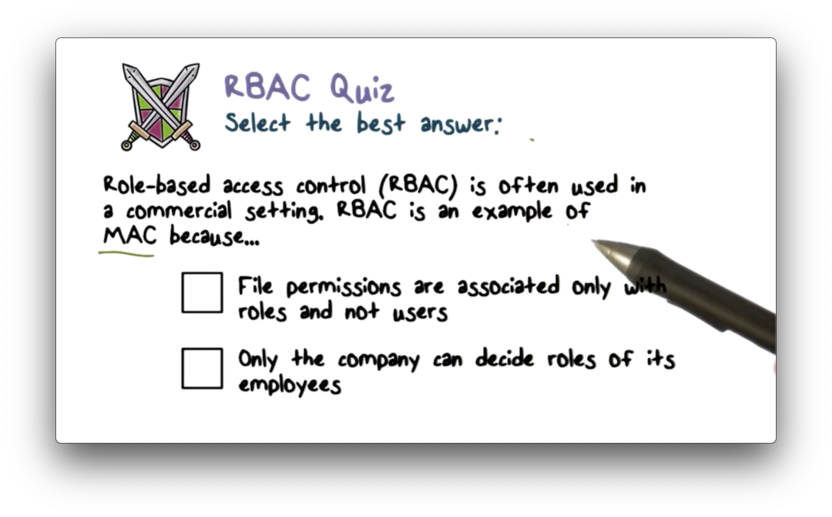
RBAC Quiz Solution
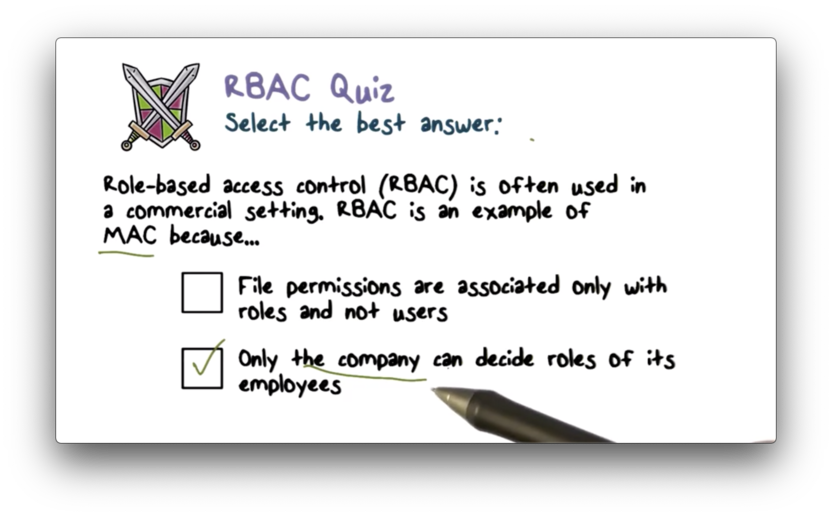
In mandatory access control, the company decides who can share what.
MAC Support Quiz
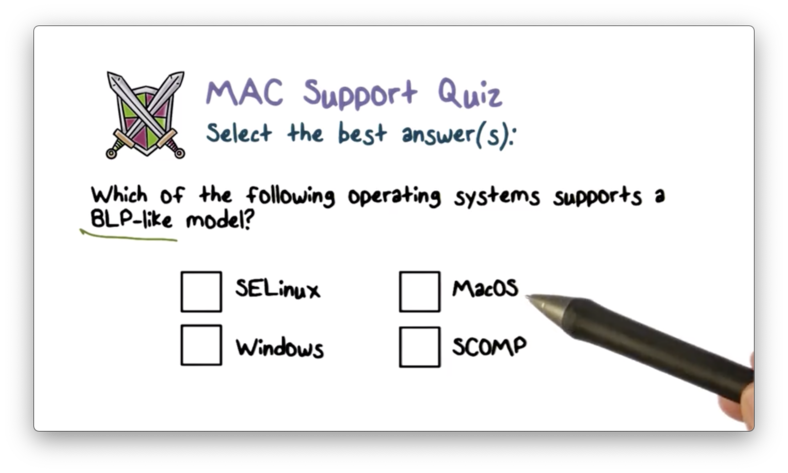
MAC Support Quiz Solution

Least Privilege Quiz

Least Privilege Quiz Solution

The TCB provides high assurance, not certainty.
TCB High Assurance Quiz

TCB High Assurance Quiz Solution

Security by obscurity violates open design.
Design Principle Quiz
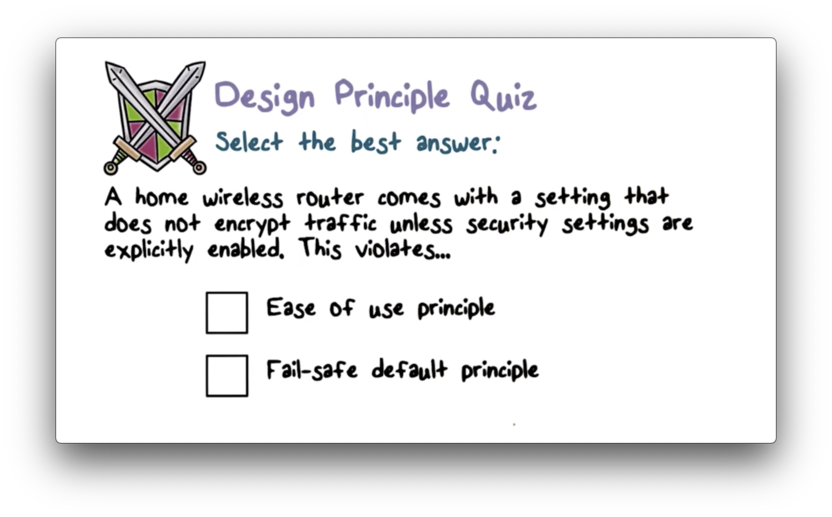
Design Principle Quiz Solution
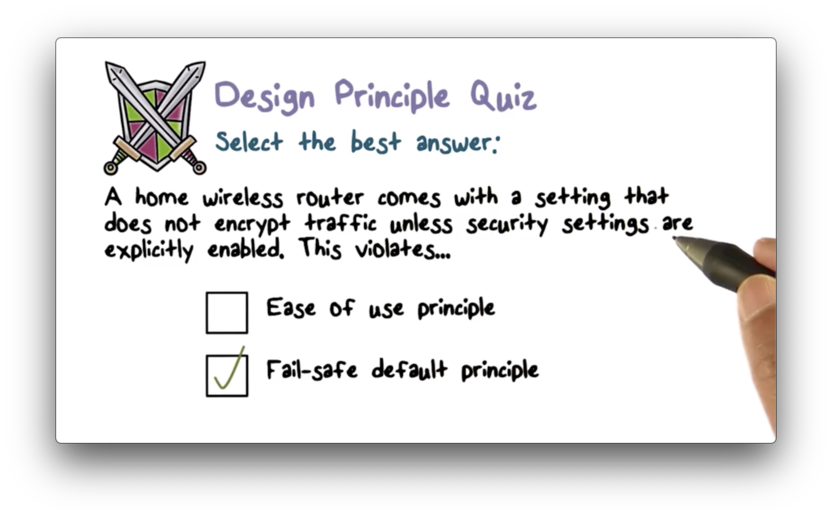
A fail-safe default is one that provides security unless otherwise specified. In this case, the default should be traffic encryption.
Reducing TCB Size Quiz

Reducing TCB Size Quiz Solution

Testing TCB Quiz

Testing TCB Quiz Solution
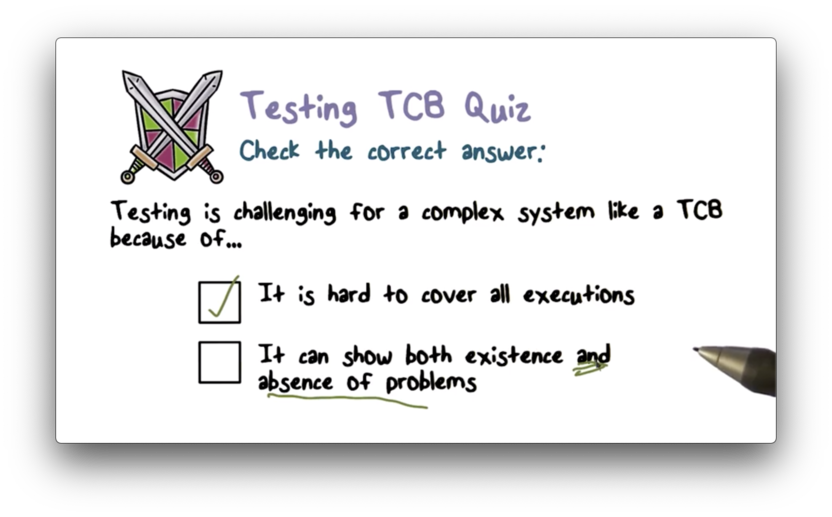
Testing can't show the absence of problems.
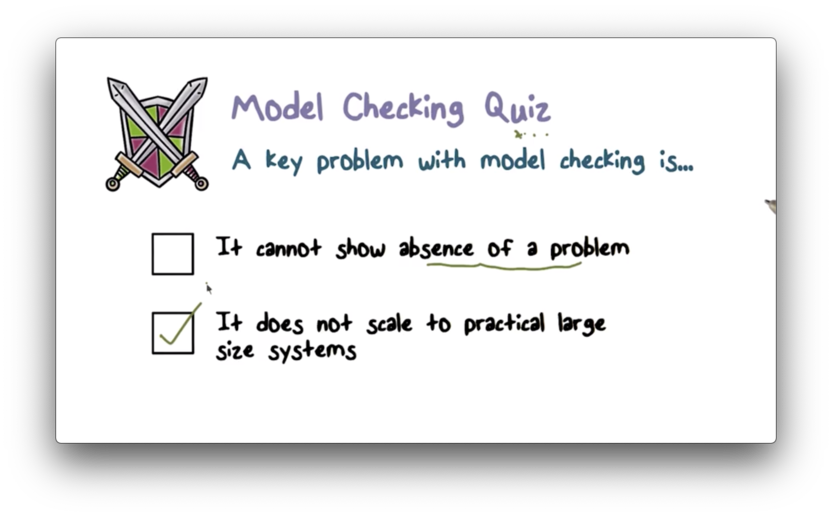
Model Checking Quiz
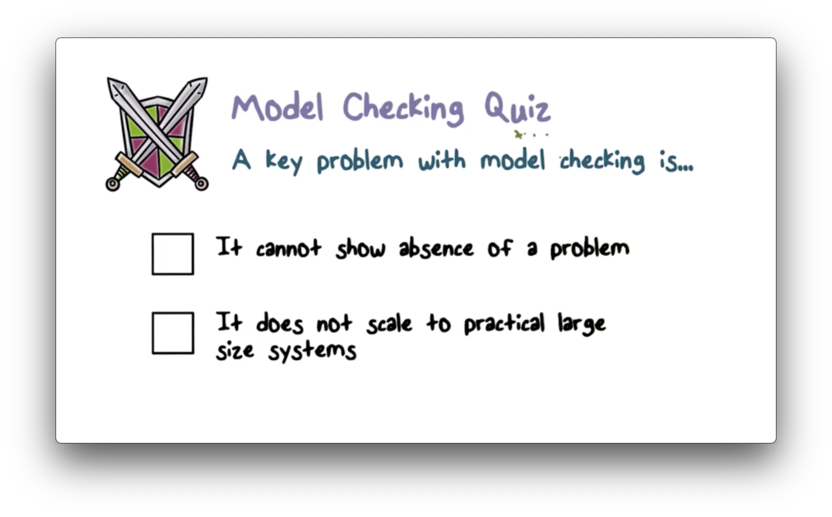
Model Checking Quiz Solution
TCSEC Divisions Quiz

TCSEC Divisions Quiz Solution

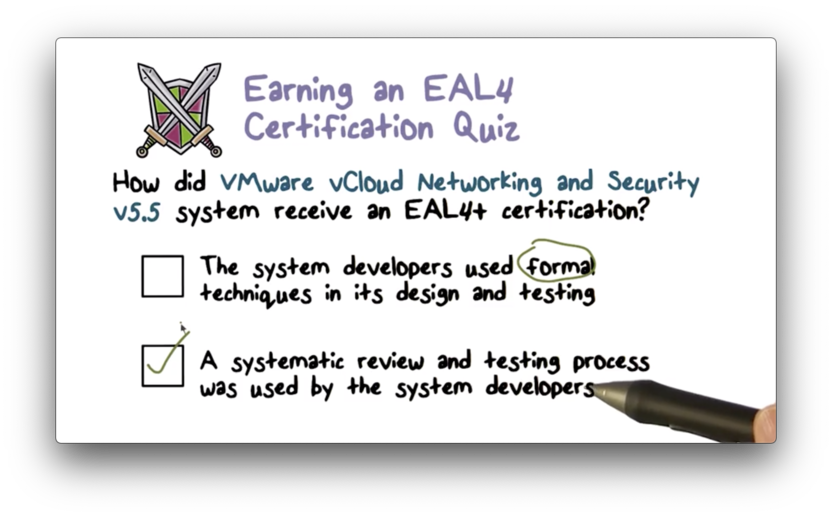
Earning an EAL4 Certification Quiz
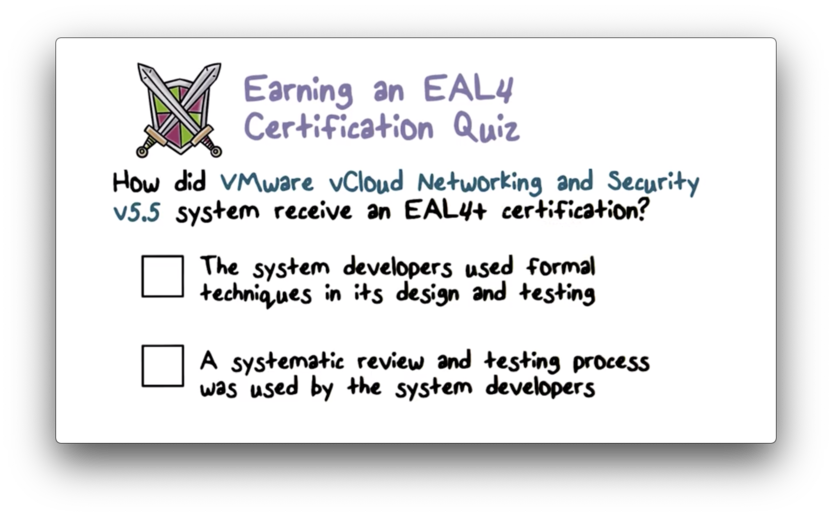
Earning an EAL4 Certification Quiz Solution
Cost Benefit Certification Tradeoffs Quiz

Cost Benefit Certification Tradeoffs Quiz Solution

Database Security
Database Threats Quiz

Database Threats Quiz Solution

Database Hacking Quiz

Database Hacking Quiz Solution

Key Value Quiz
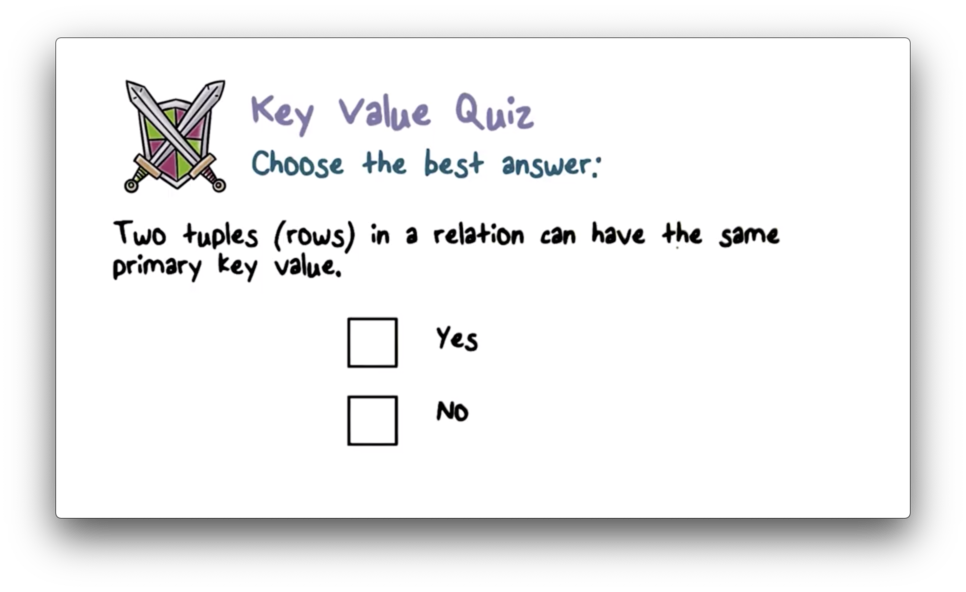
Key Value Quiz Solution
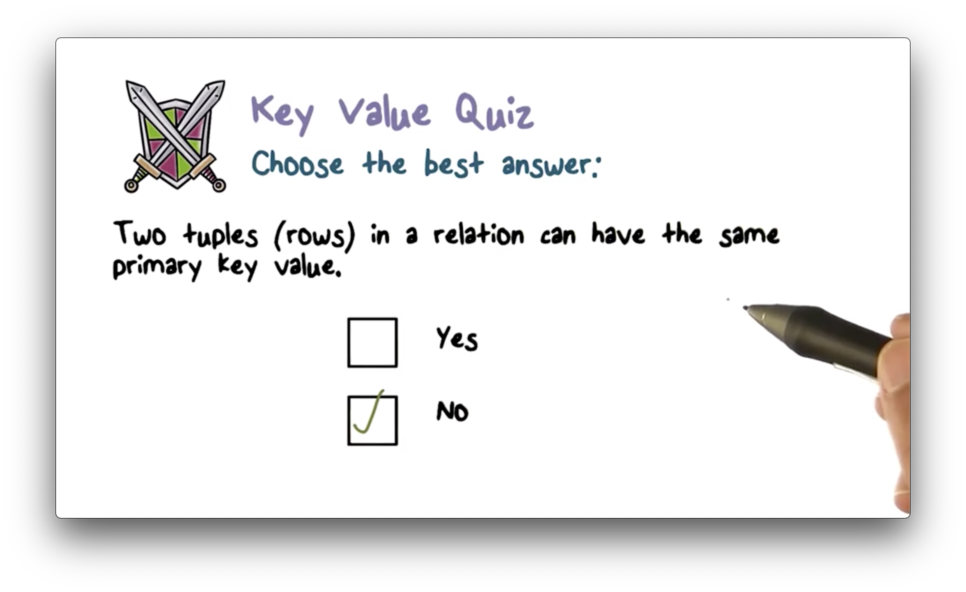
A primary key uniquely identifies a row.
Database Views Quiz
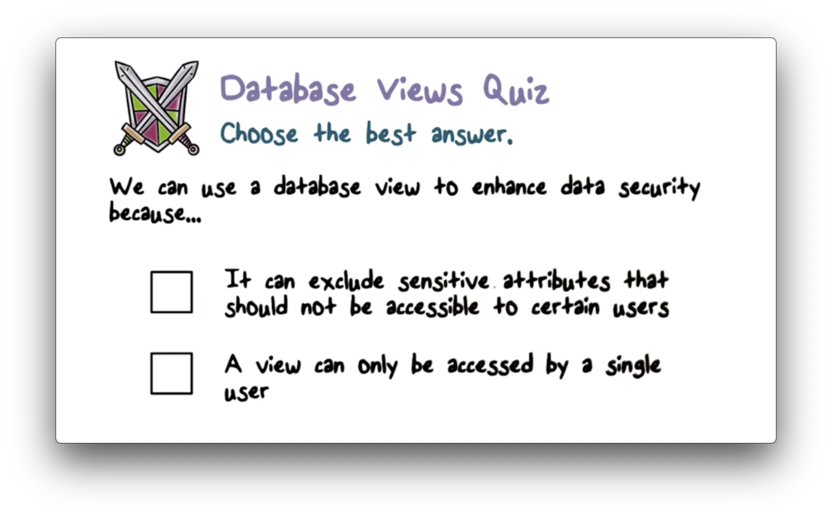
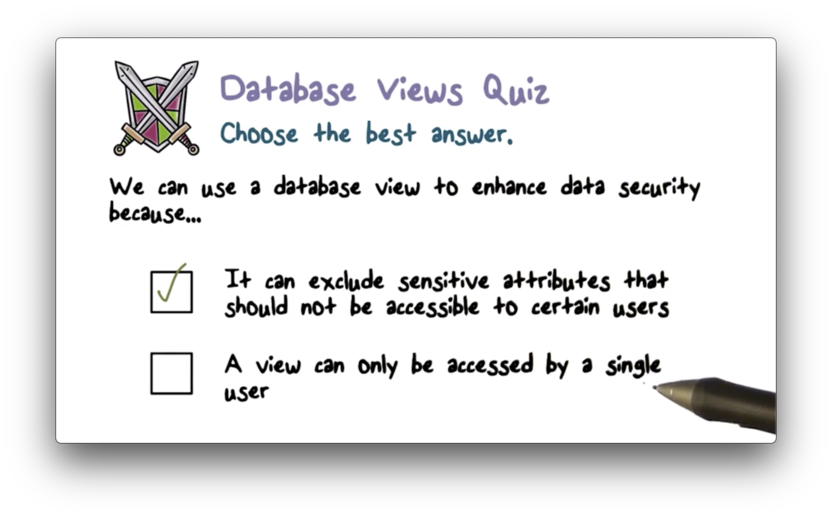
Database Views Quiz Solution
Database Access Control Quiz
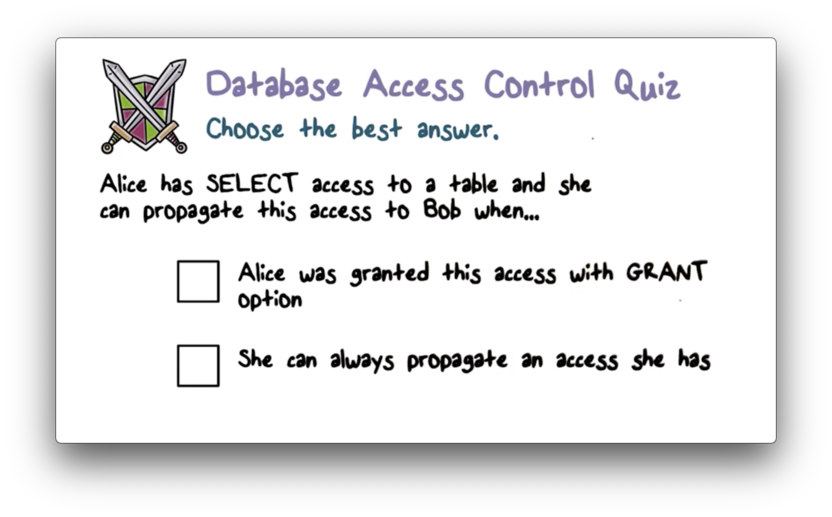
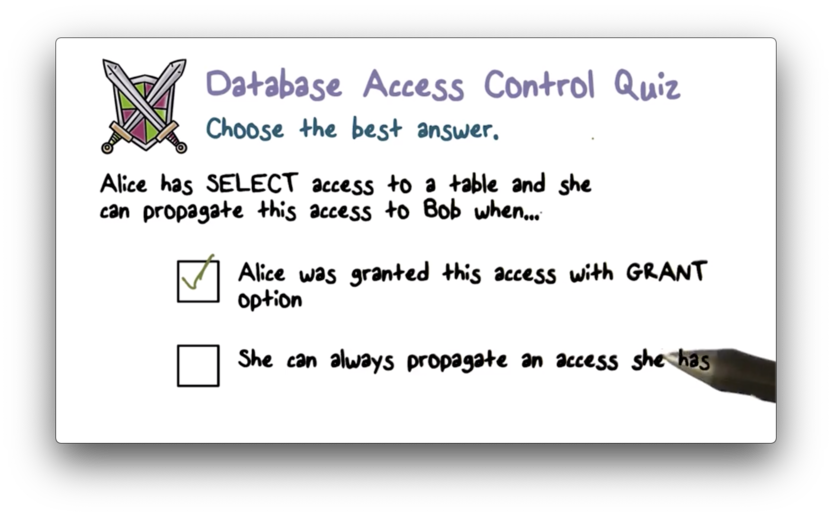
Database Access Control Quiz Solution
Cascading Authorizations Quiz

Cascading Authorizations Quiz Solution

DAC or MAC Quiz

DAC or MAC Quiz Solution

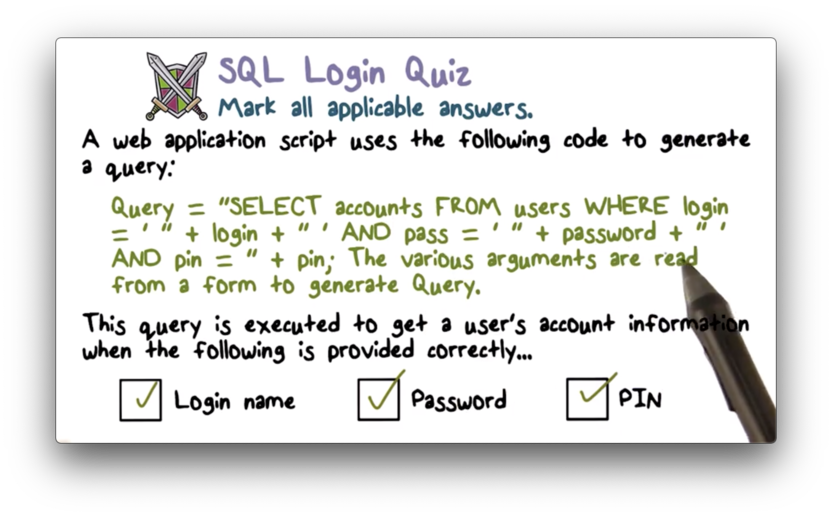
SQL Login Quiz
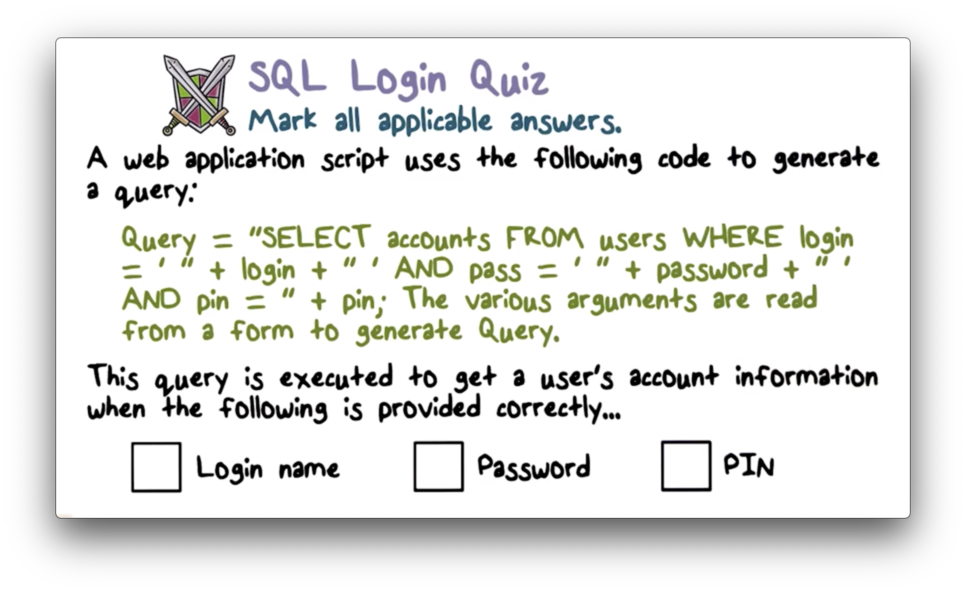
SQL Login Quiz Solution
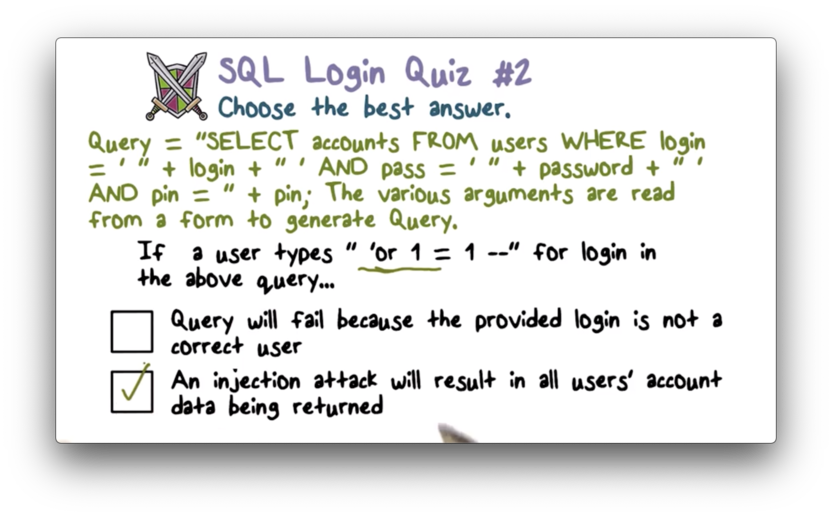
SQL Login Quiz 2
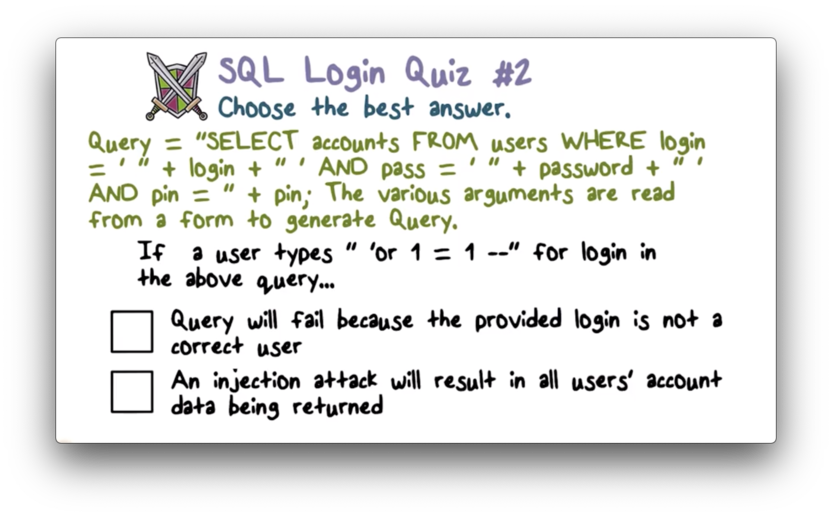
SQL Login Quiz 2 Solution
SQL Inference Attack Quiz

SQL Inference Attack Quiz Solution

SQL Inference Attack Quiz 2

SQL Inference Attack Quiz 2 Solution

Consider the case where one student from a region containing two students retrieves the grade information about that region.
Malicious Code
What is Malware Quiz

What is Malware Quiz Solution

Host Required Malware Quiz 1

Host Required Malware Quiz 1 Solution

Host Required Malware Quiz 2

Host Required Malware Quiz 2 Solution

Types of Viruses Quiz

Types of Viruses Quiz Solution

Macro viruses run when an infected document is opened with a given application. Boot sector viruses run before the operating system is loaded.
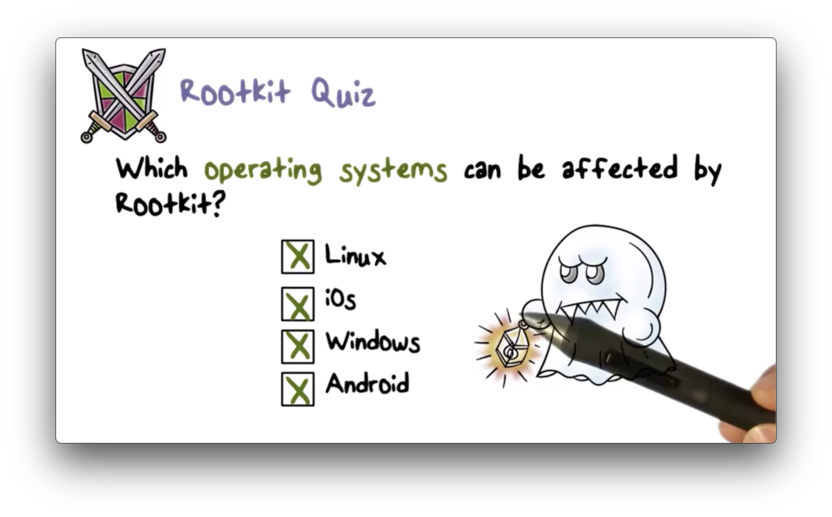
Rootkit Quiz
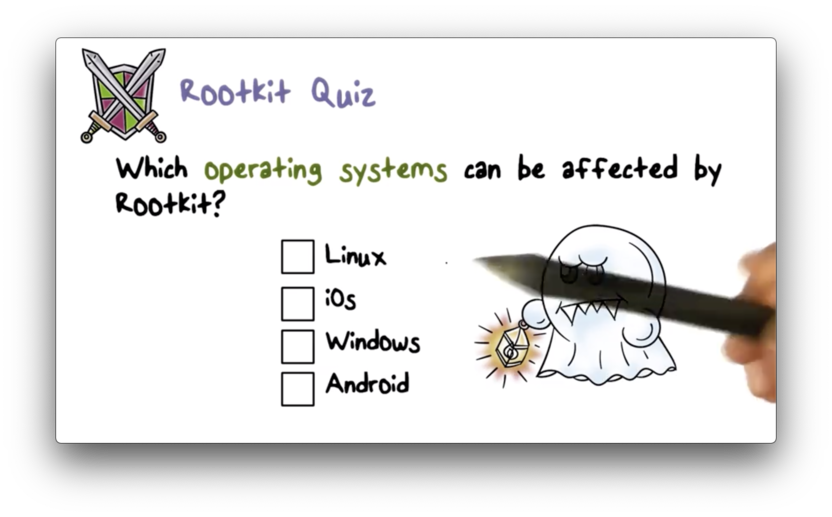
Rootkit Quiz Solution
Truth and Misconceptions Quiz

Truth and Misconceptions Quiz Solution

Worm Quiz

Worm Quiz Solution

Malware Prevention & Detection Quiz

Malware Prevention & Detection Quiz Solution

Most Expensive Worm Quiz

Most Expensive Worm Quiz Solution

Modern Malware
Bot Quiz

Bot Quiz Solution

DDoS Quiz
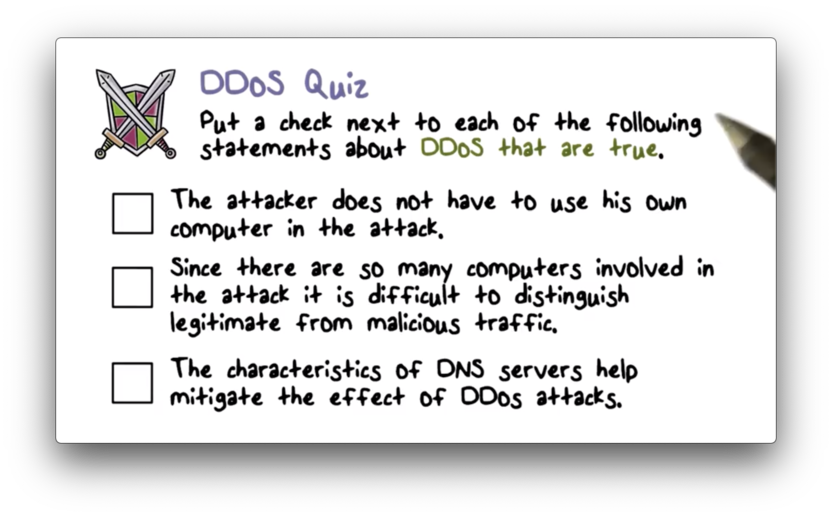
DDoS Quiz Solution
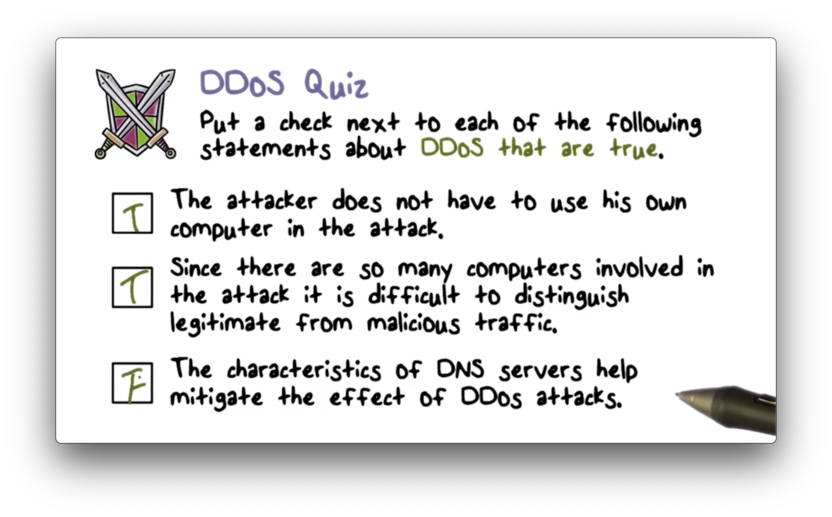
Remember, the characteristics of DNS servers can be used to amplify the effects of DDoS attacks, not mitigate them.
C&C Design Quiz

C&C Design Quiz Solution

The second answer is false. Bot code can have logic bombs or other triggers that enable bot to attack without contacting a C&C server.
The third answer is also false. A botnet is more likely to be found using custom communication protocols, as admins observing the network are more likely to detect strange types of traffic flowing from their system.
Botnet C&C Quiz

Botnet C&C Quiz Solution

A single gmail account, hardcoded in bot code, is both easy to detect and easy to disrupt.
P2P traffic will easily stand out in an enterprise network where peer-to-peer communications are not typically allowed.
A news site can be hard to detect, because traffic to news websites is common. However, if the site is identified as being malicious, it can easily be blocked.
APT Quiz

APT Quiz Solution

Malware Analysis Quiz

Malware Analysis Quiz Solution

Firewalls
Firewalls Quiz

Firewalls Quiz Solution

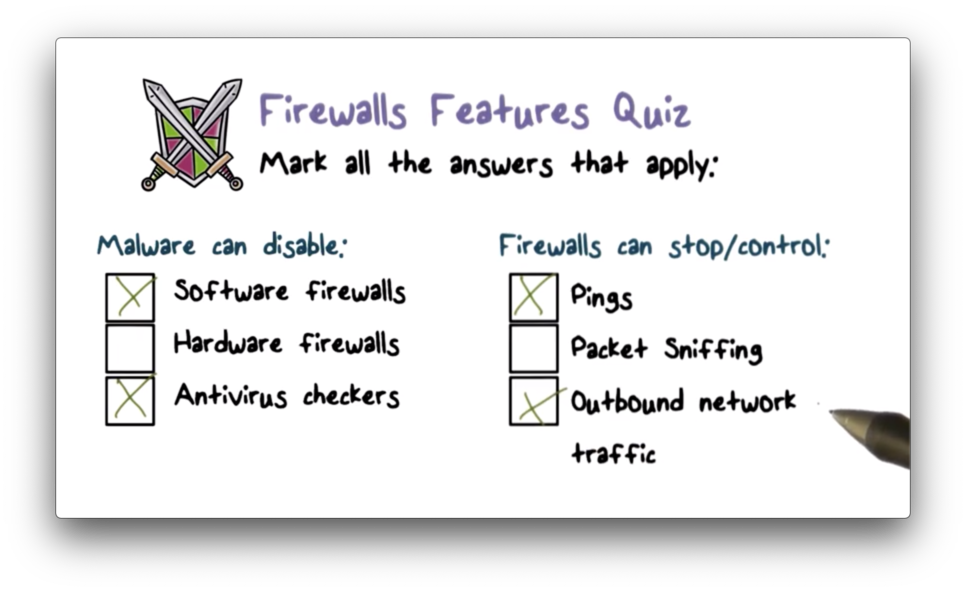
Firewall Features Quiz
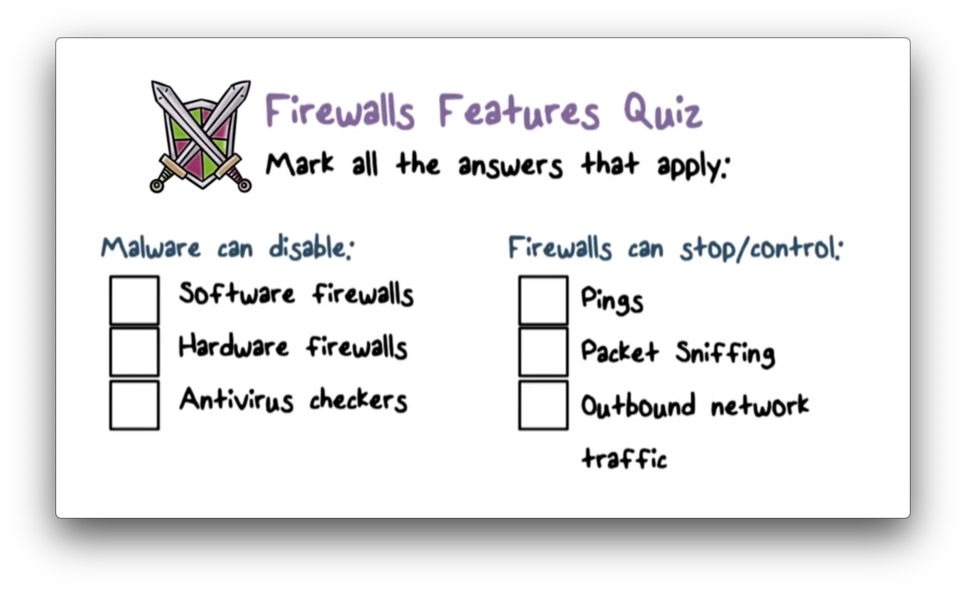
Firewall Features Quiz Solution
Firewall Filtering Quiz
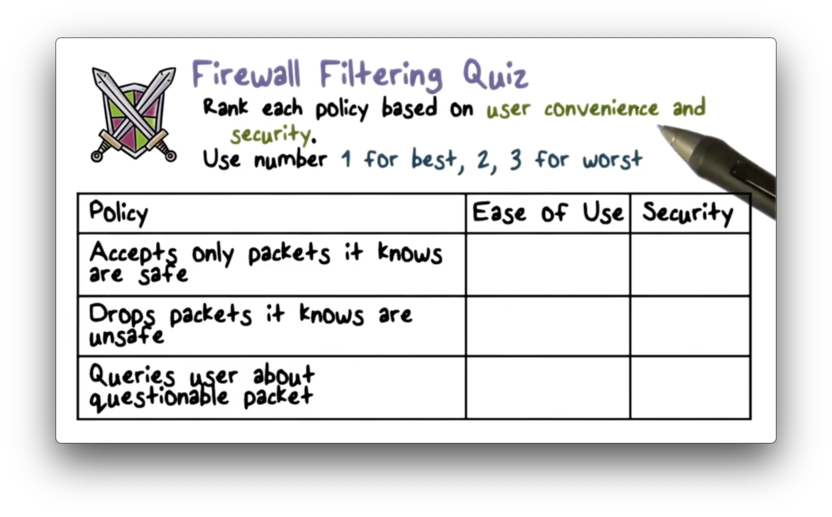
Firewall Filtering Quiz Solution
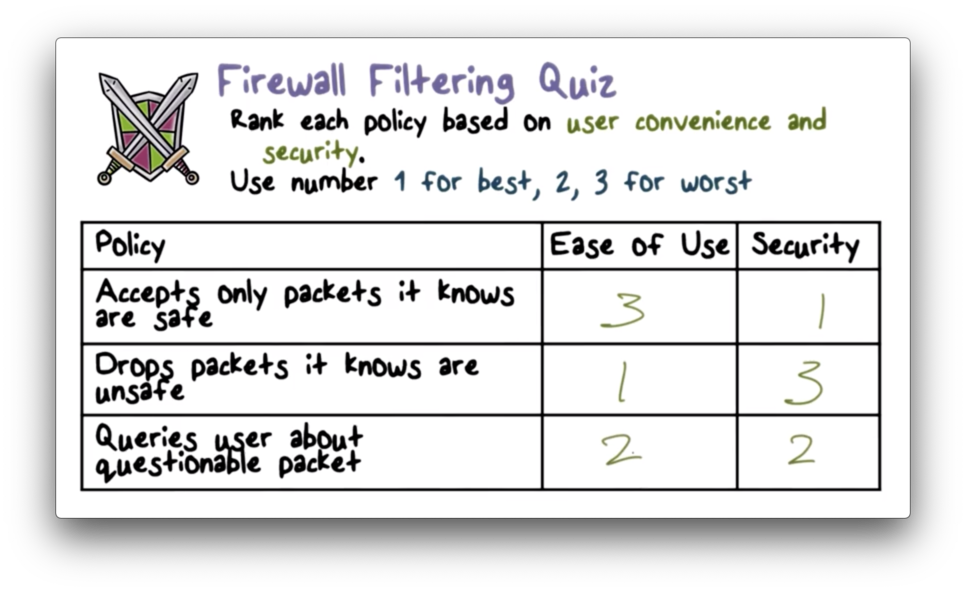
The first example follows the "default drop" rule, which is high security but requires new services to be expressly allowed. The second example follows the "default forward" rule, which is easier to use at the expense of security. The final approach sits in between the two in terms of security and ease of use.
Packet Filtering Quiz

Packet Filtering Quiz Solution

Filtering Quiz

Filtering Quiz Solution

Personal Firewalls Quiz

Personal Firewalls Quiz Solution

If the device is not always protected by the corporate network, as is the case in scenarios 1 and 3, then the personal firewall is needed for additional security.
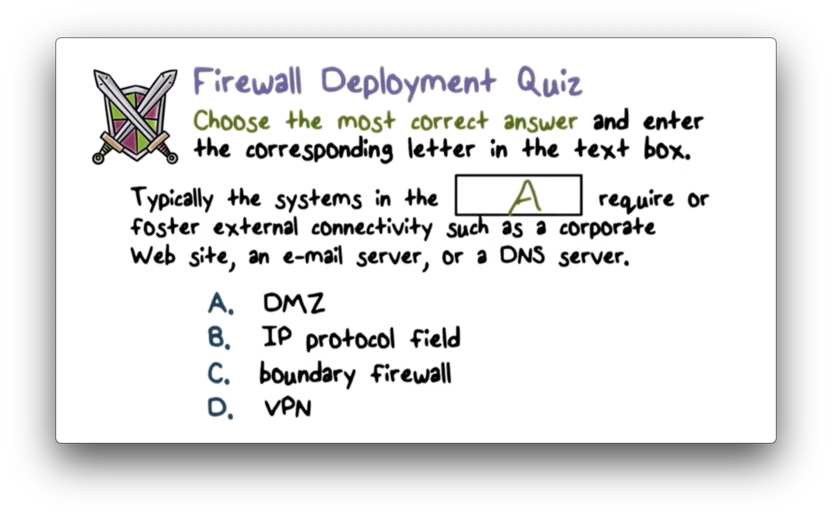
Firewall Deployment Quiz
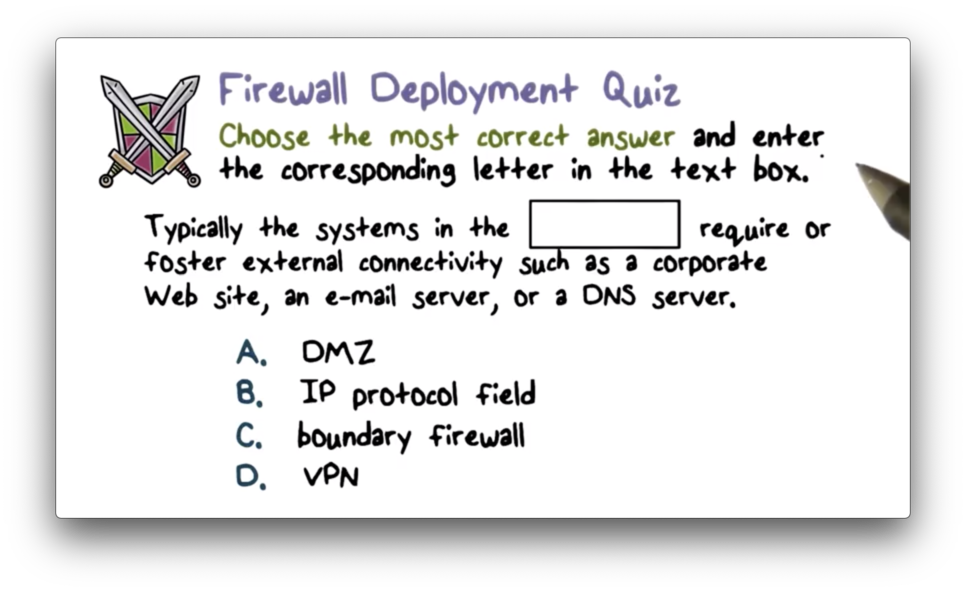
Firewall Deployment Quiz Solution
Stand Alone Firewall Quiz

Stand Alone Firewall Quiz Solution

Intrusion Detection
Intrusion Detection Quiz

Intrusion Detection Quiz Solution

Intruder Quiz

Intruder Quiz Solution

Types of Backdoors Quiz

Types of Backdoors Quiz Solution

Read more here, here, and here.
Analysis Detection Quiz

Analysis Detection Quiz Solution

Signature Detection Quiz

Signature Detection Quiz Solution

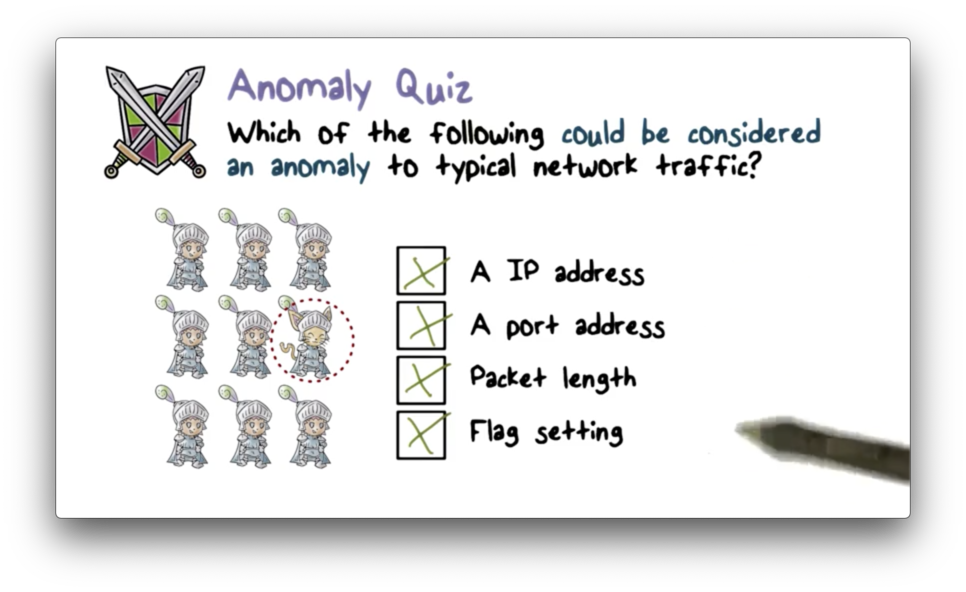
Anomaly Quiz
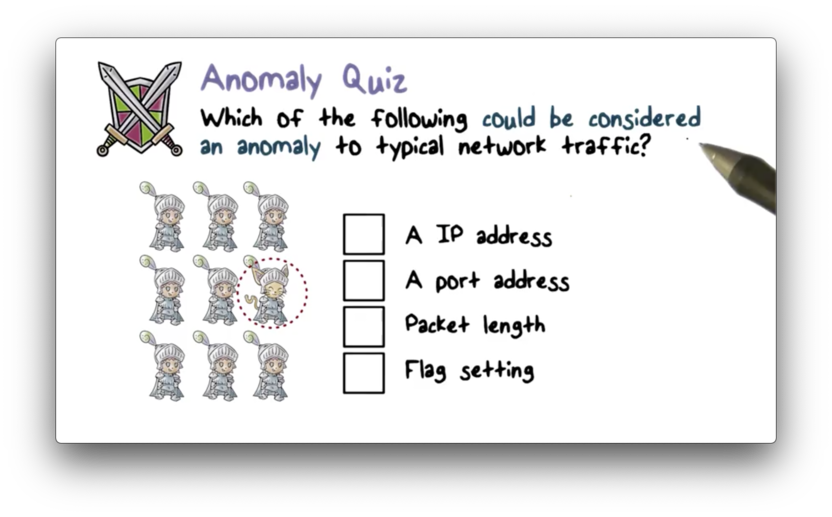
Anomaly Quiz Solution
Statistical & Knowledge Based Approaches Quiz

Statistical & Knowledge Based Approaches Quiz Solution

Machine Learning Quiz

Machine Learning Quiz Solution

Anomalous Behavior Quiz

Anomalous Behavior Quiz Solution

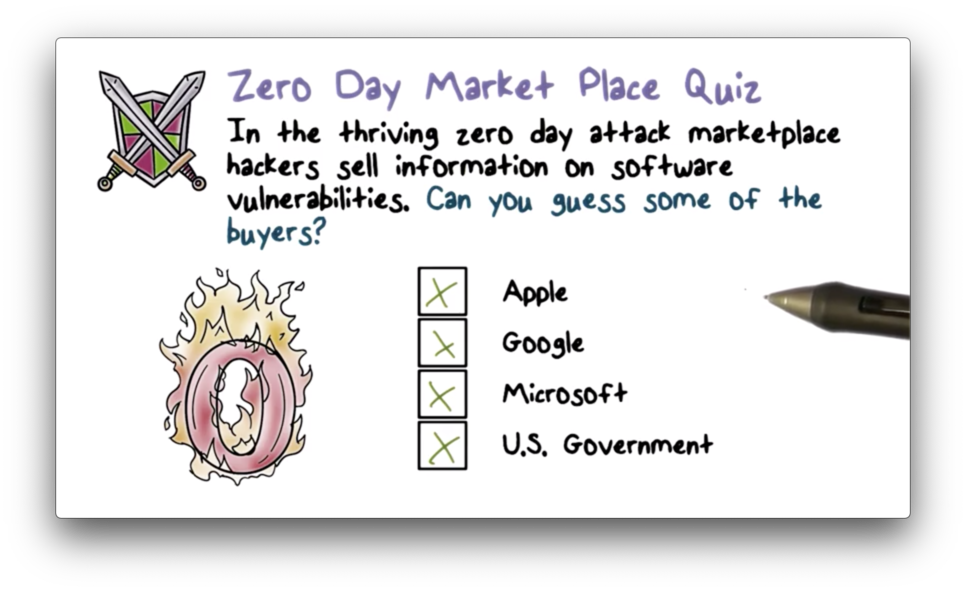
Zero Day Market Place Quiz

Zero Day Market Place Quiz Solution
Attacks Quiz

Attacks Quiz Solution

NIDS Quiz

NIDS Quiz Solution

IDS Quiz

IDS Quiz Solution

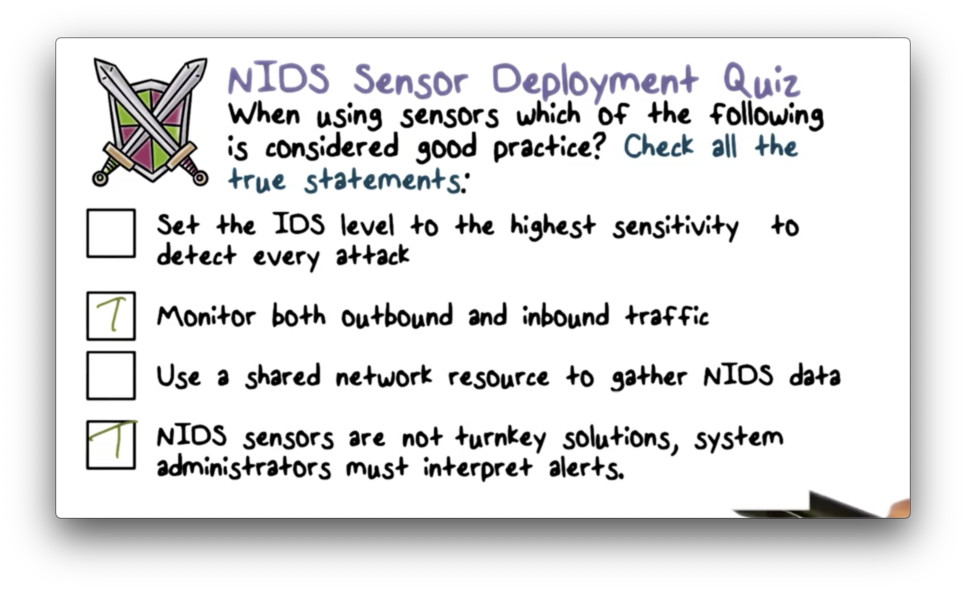
NIDS Sensor Deployed Quiz
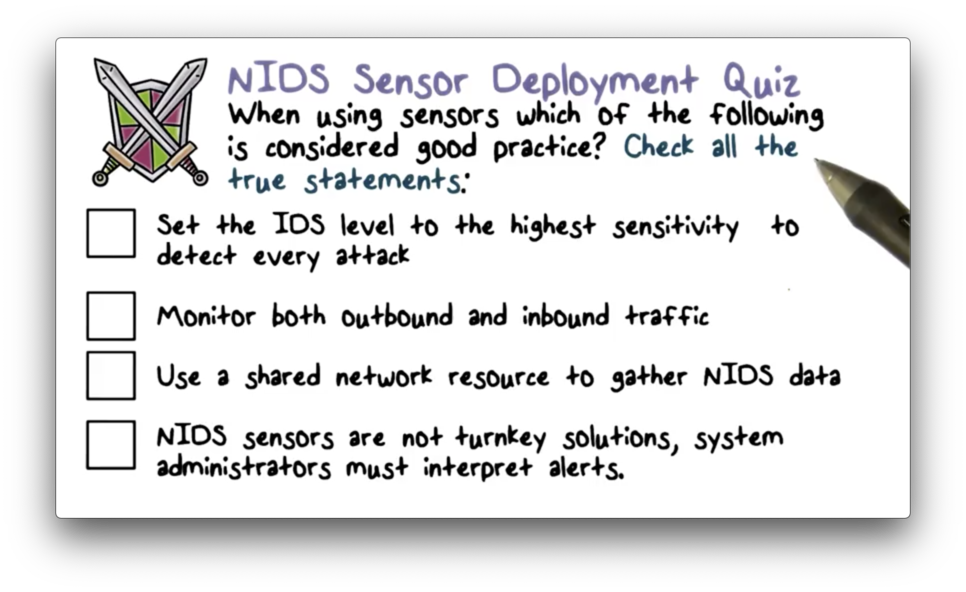
NIDS Sensor Deployed Quiz Solution
Snort Quiz

Snort Quiz Solution

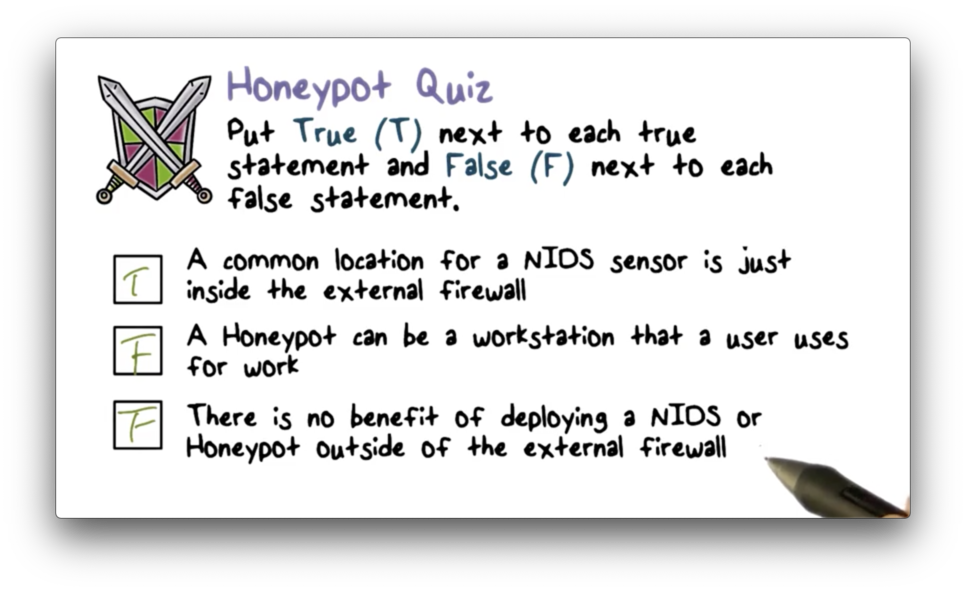
Honeypot Quiz
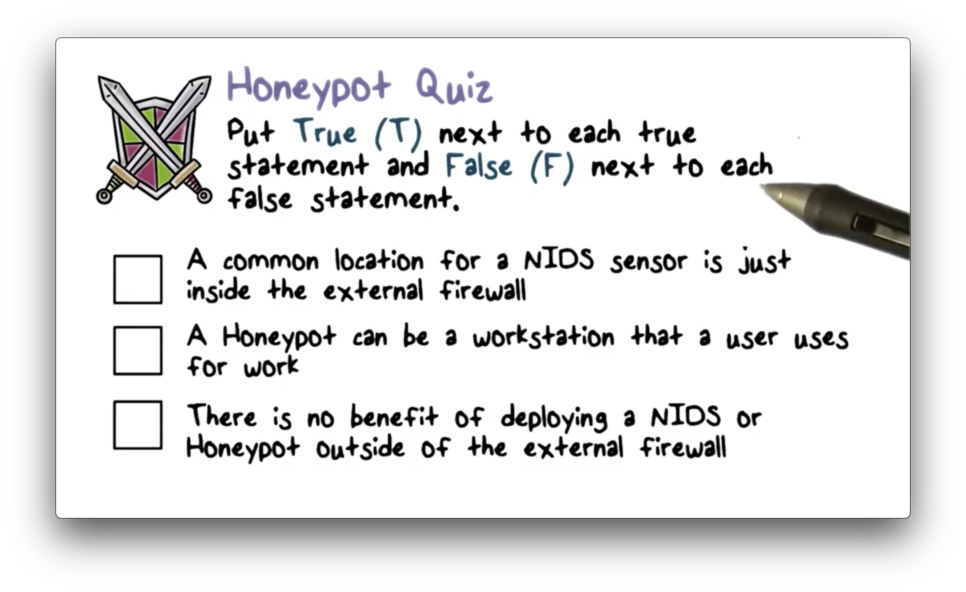
Honeypot Quiz Solution
IDS Quiz
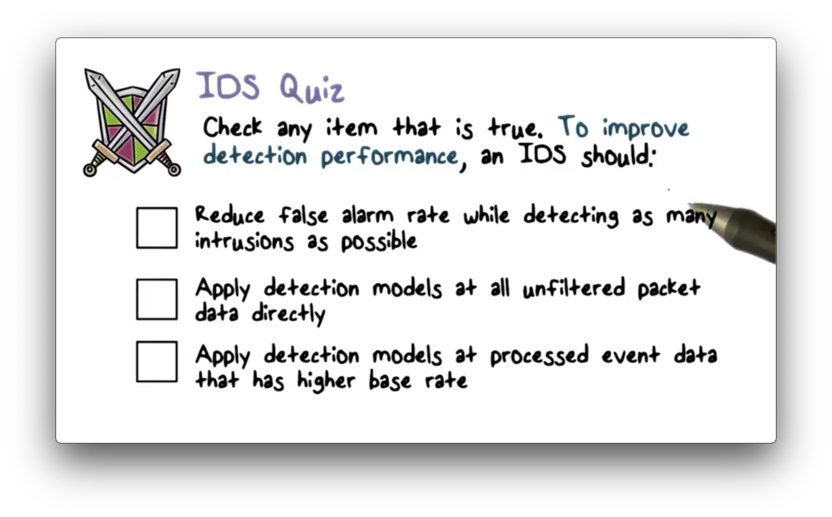
IDS Quiz Solution

IDS Attack Quiz

IDS Attack Quiz Solution

Introduction to Cryptography
Encryption Attack Quiz
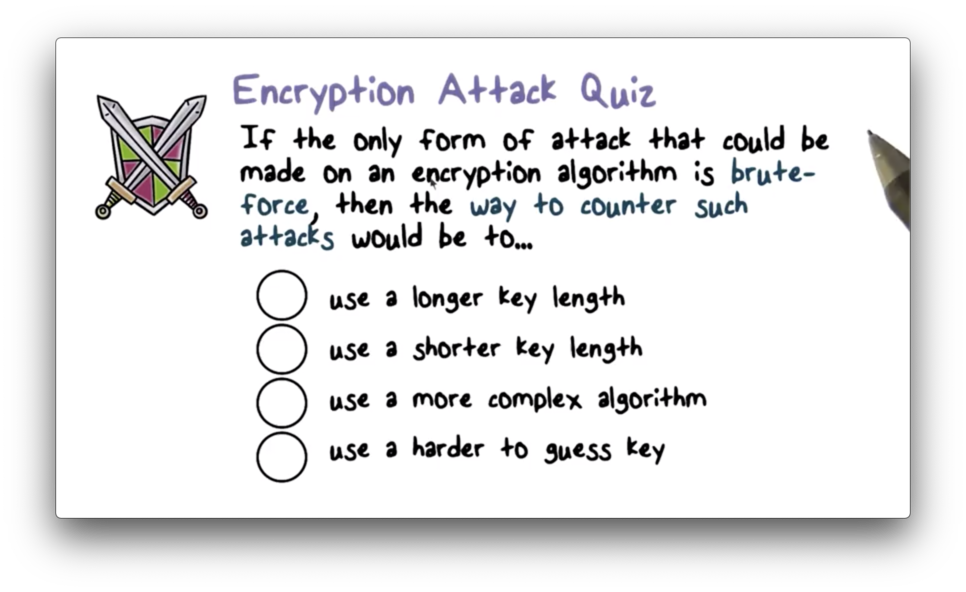
Encryption Attack Quiz Solution
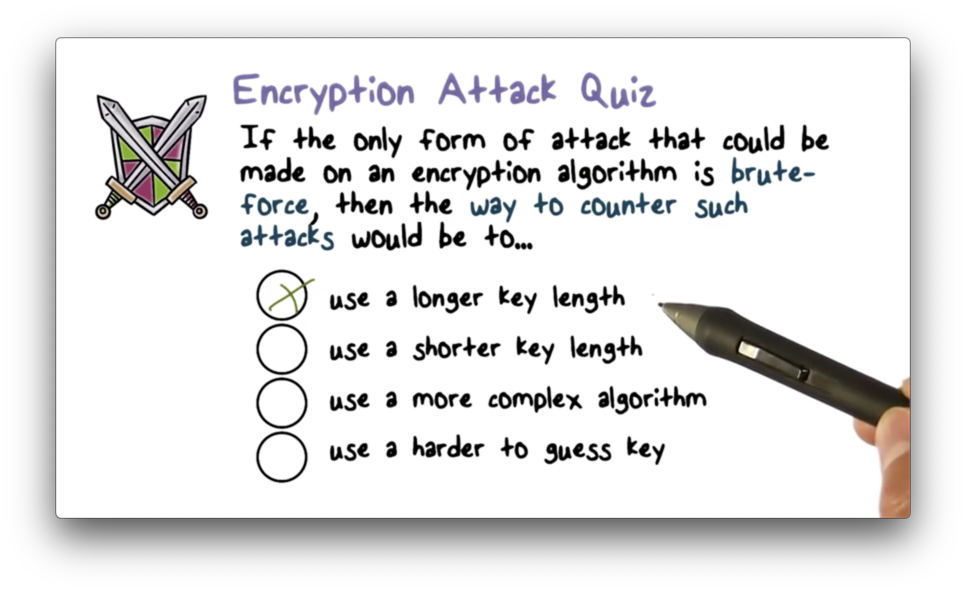
In a brute-force attack, the attacker must try all potential keys. The only way to make this task more difficult is to increase the length of the key, thus increasing the size of the keyspace.
Simple Ciphers Quiz

Simple Ciphers Quiz Solution

Since "A" maps to "D", "B" maps to "E", and so forth, we can just "rewind" each letter in the ciphertext by three to obtain the plaintext.
Monoalphabetic Cipher Quiz

Monoalphabetic Cipher Quiz Solution

Vigenere Cipher Quiz

Vigenere Cipher Quiz Solution

Hash Function Quiz
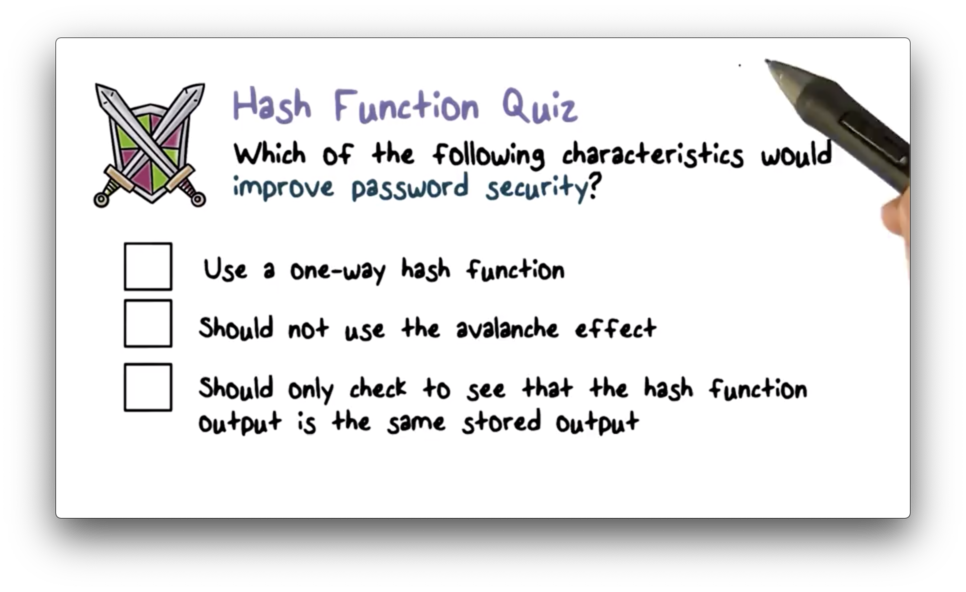
Hash Function Quiz Solution
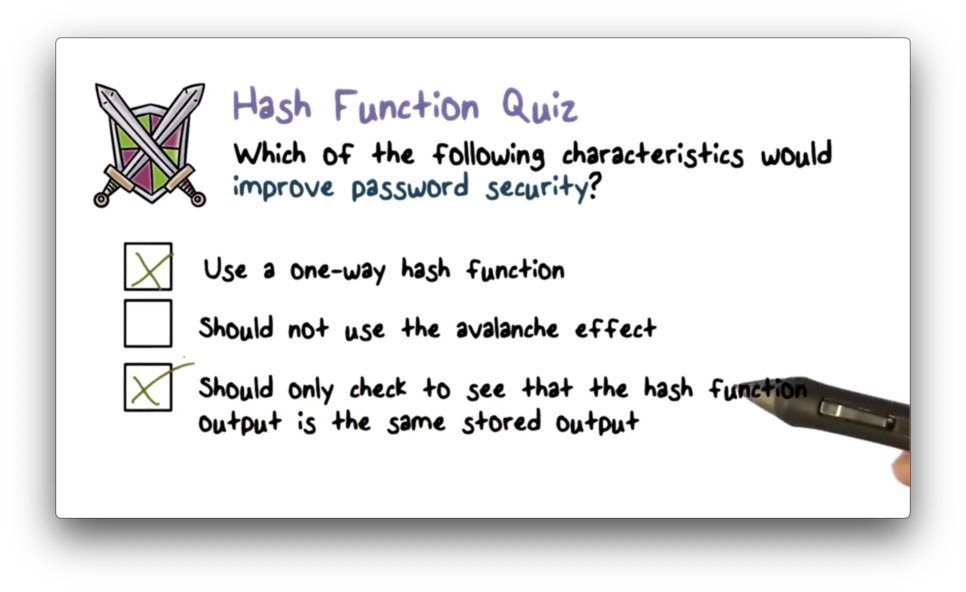
The avalanche effect states that a small change in the input to a hash function causes a large change to the output. We want this in place as a way to obscure similar passwords. Without the avalanche effect, an attacker may be able to deduce password A from its hash value if he knows that the hash of a string B is similar to A's hash.
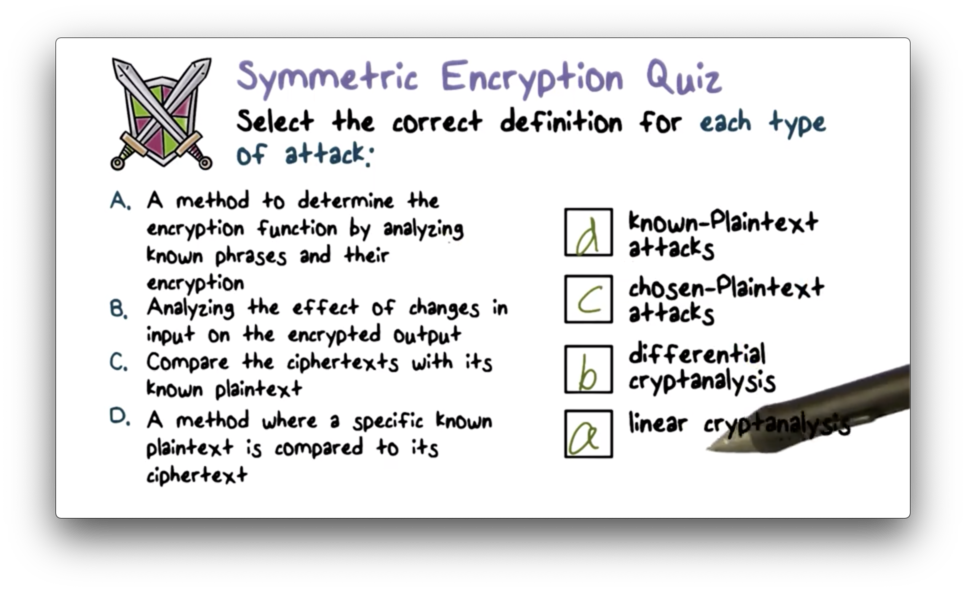
Symmetric Encryption Quiz

Symmetric Encryption Quiz Solution
Asymmetric Encryption Quiz

Asymmetric Encryption Quiz Solution

Encryption Quiz

Encryption Quiz Solution

Symmetric Encryption
Block Cipher Quiz
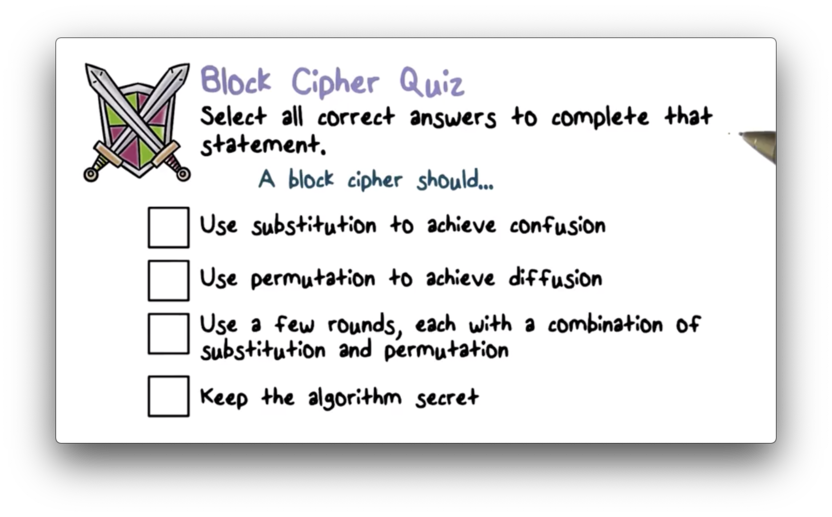
Block Cipher Quiz Solution

XOR Quiz
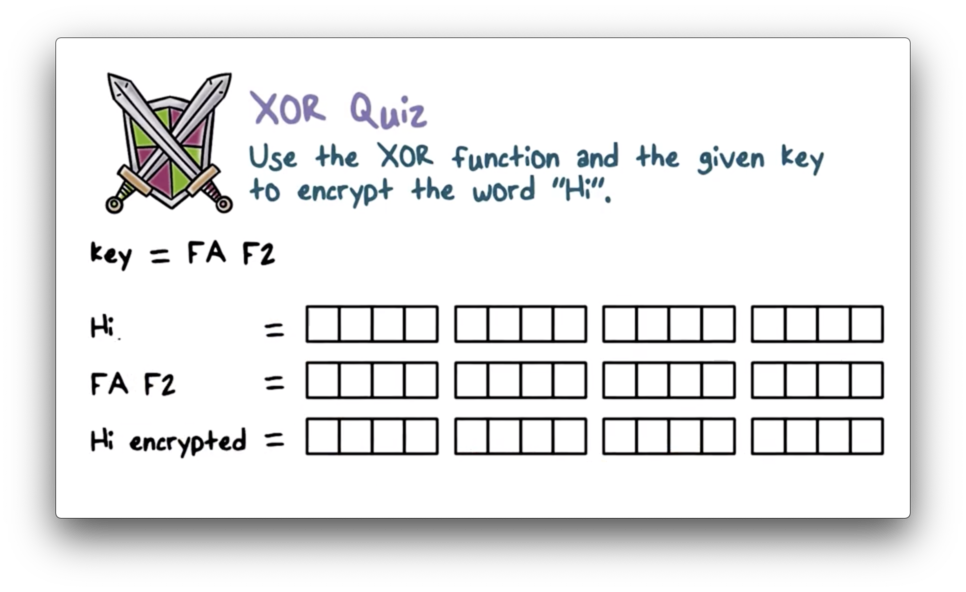
XOR Quiz Solution
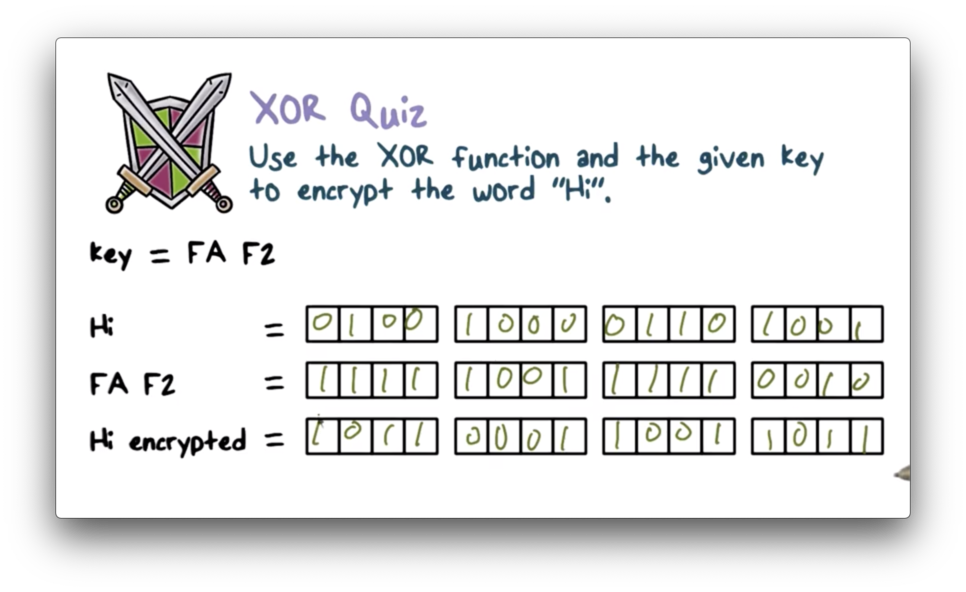
"H" has an ASCII code of 72, which maps to 0b01001000, and "i" has an ASCII code of 105, which maps to 0b01101001. "F" maps to 15 (0b1111) and "A" maps to 11 (0b1001), so "FA" maps to 0b11111001 and "F2" maps to 0b11111001.
We XOR two numbers bit-by-bit, and we return 0 when the bits match and 1 otherwise. Therefore 0b0100100001101001 XOR 0b1111100111110010 is 0b1011000110011011.
S Box Quiz
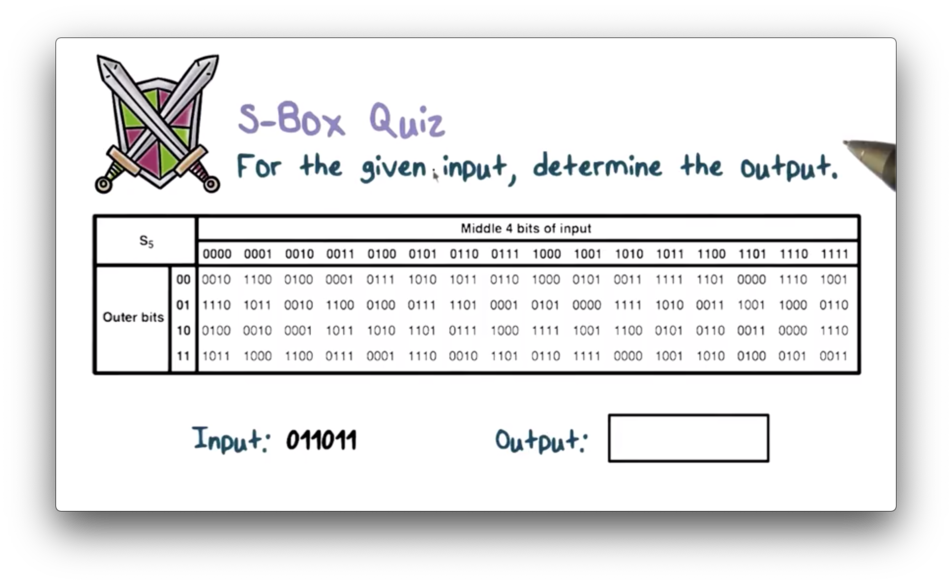
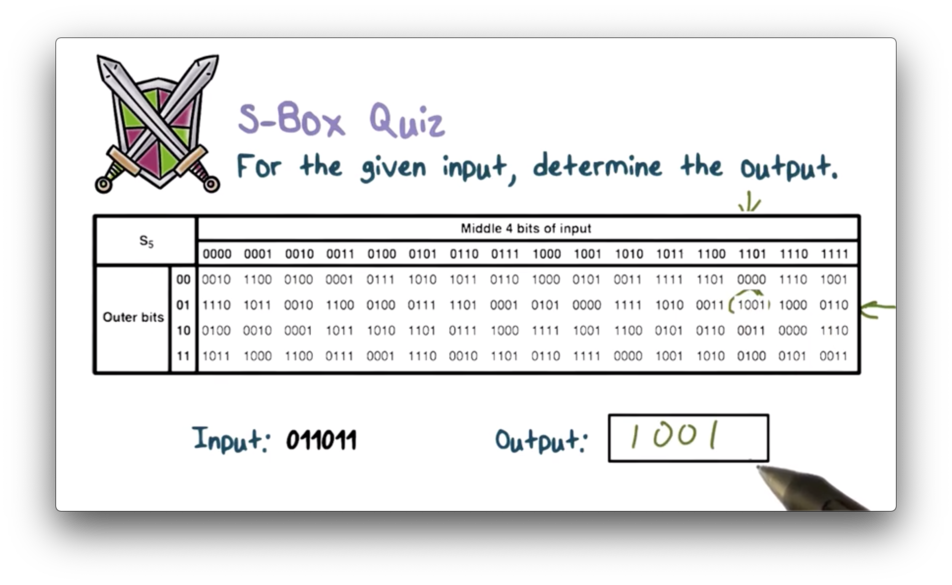
S Box Quiz Solution
DES Quiz

DES Quiz Solution

AES Encryption Quiz

AES Encryption Quiz Solution

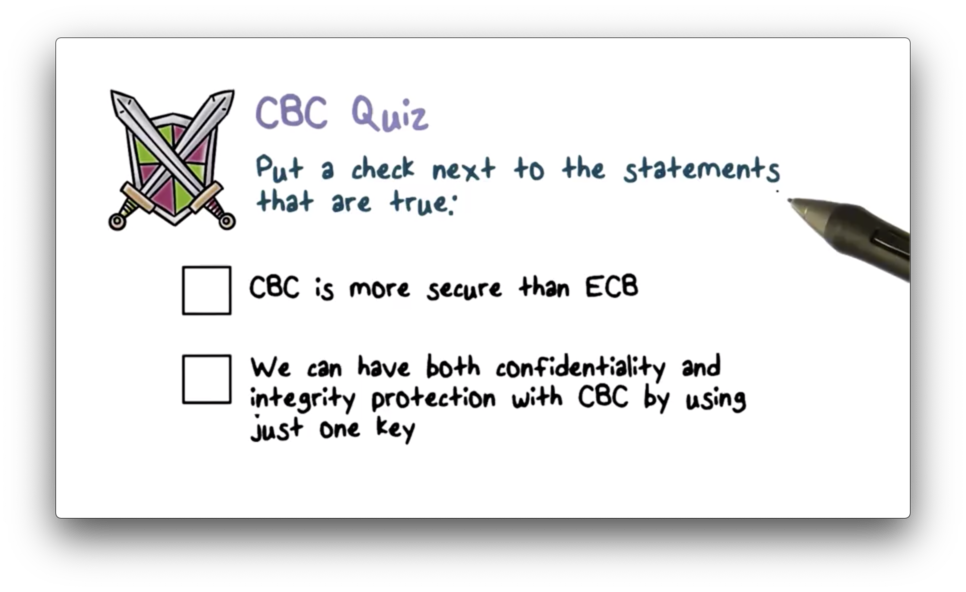
CBC Quiz
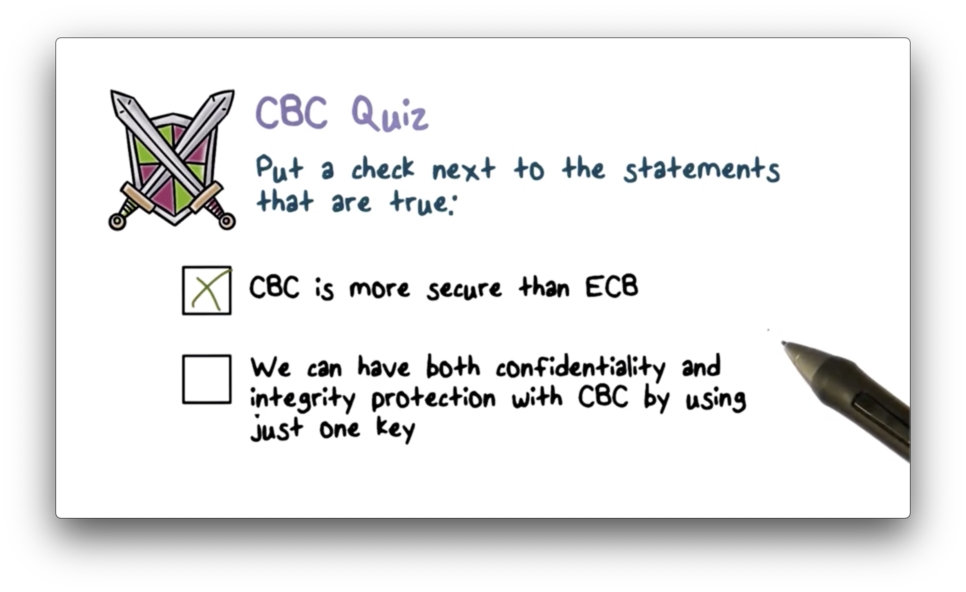
CBC Quiz Solution
Public-Key Cryptography
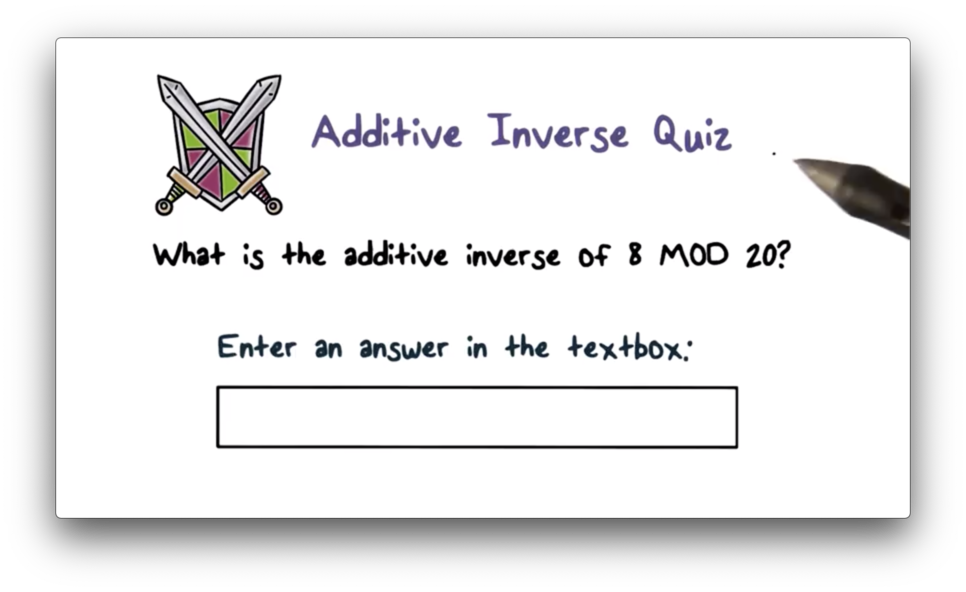
Additive Inverse Quiz
Additive Inverse Quiz Solution
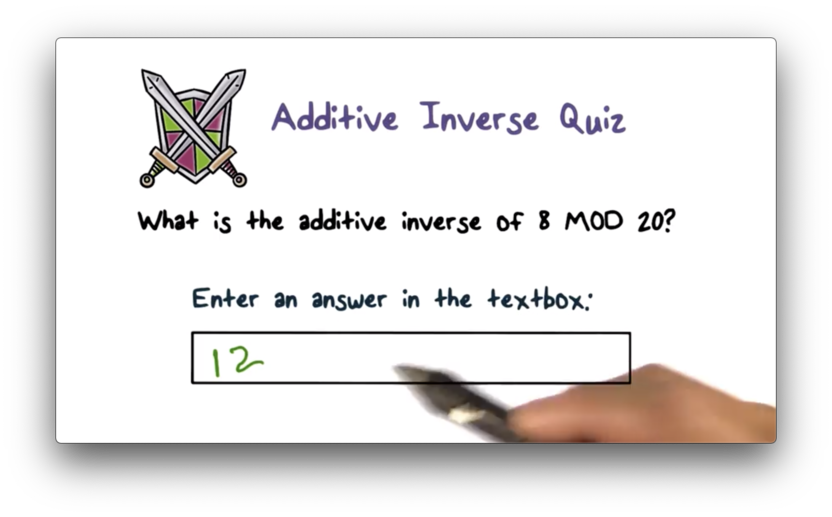
In modular addition, a number has an inverse such that . In this case, and . Therefore, because .
Modular Multiplication Quiz
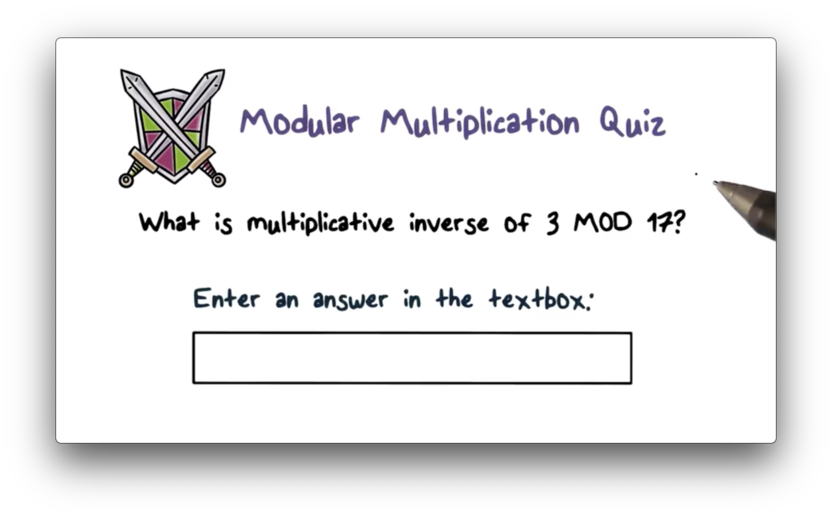
Modular Multiplication Quiz Solution
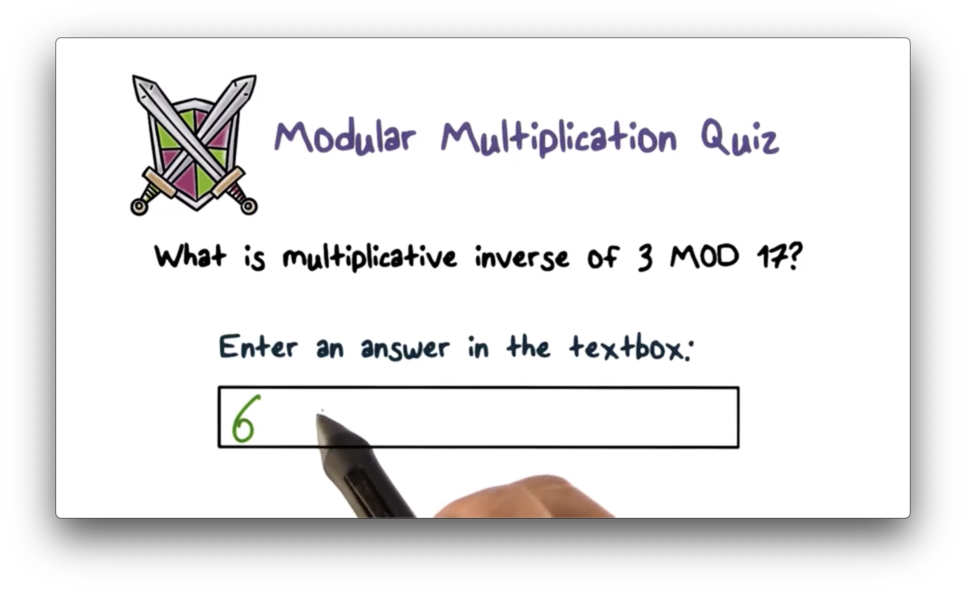
In modular multiplication, a number has an inverse such that . In this case, and . Therefore, because .
Totient Quiz

Totient Quiz Solution
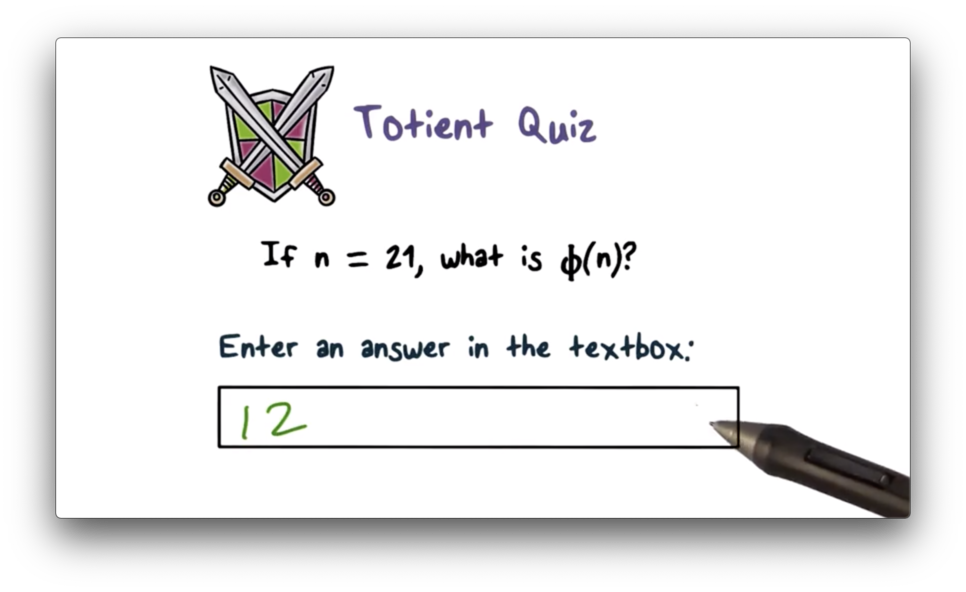
If and and are prime, then . For , and , .
Modular Exponentiation Quiz
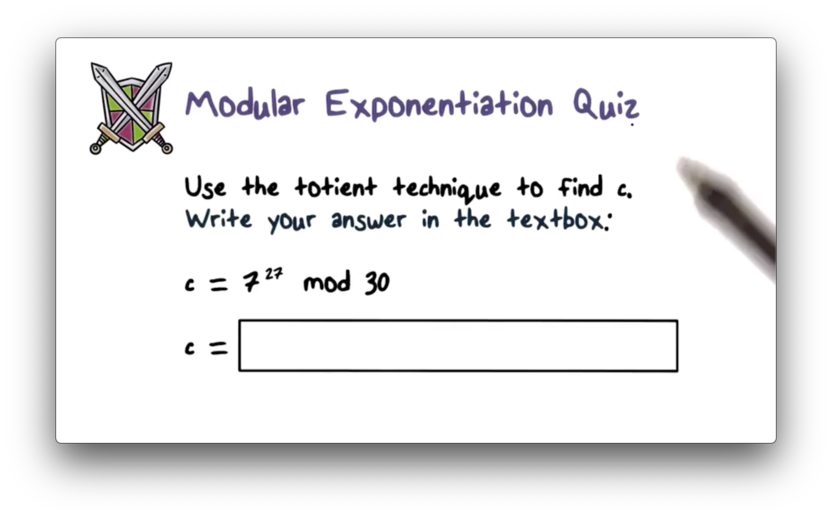
Modular Exponentiation Quiz Solution
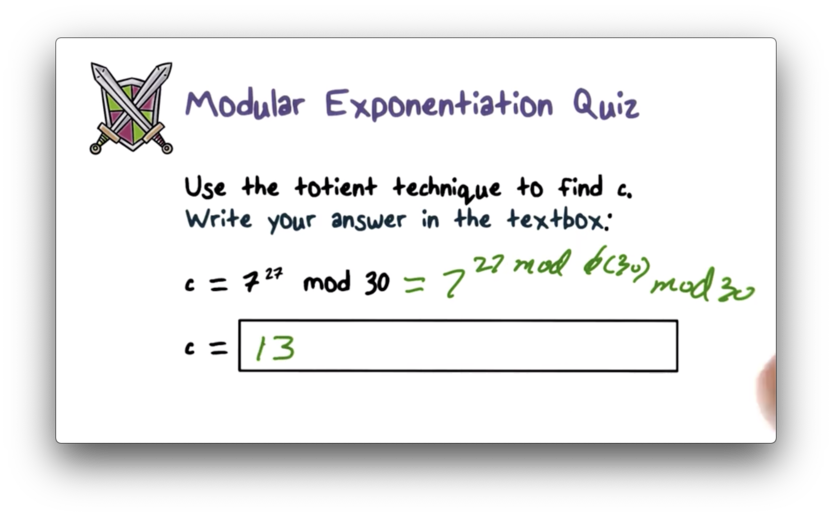
We know that . For , and , . We can calculate as follows: . Thus, . If we divide 27 by 8, we are left with a remainder of 3, so . , which yields a remainder of 13 when divided by 30.
RSA Quiz
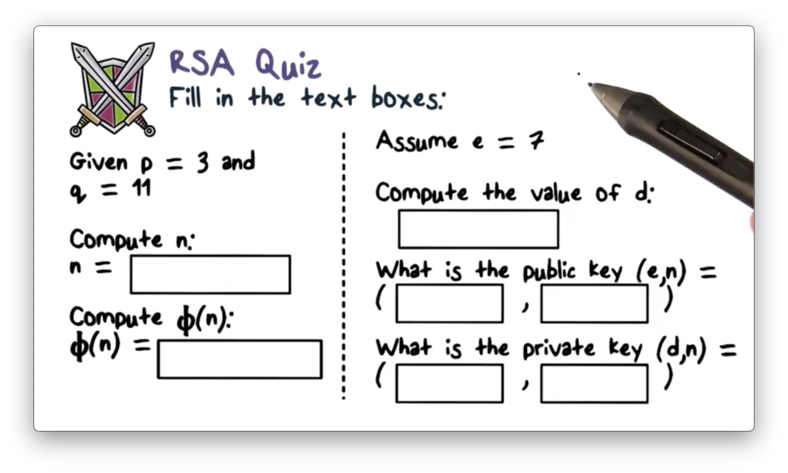
RSA Quiz Solution
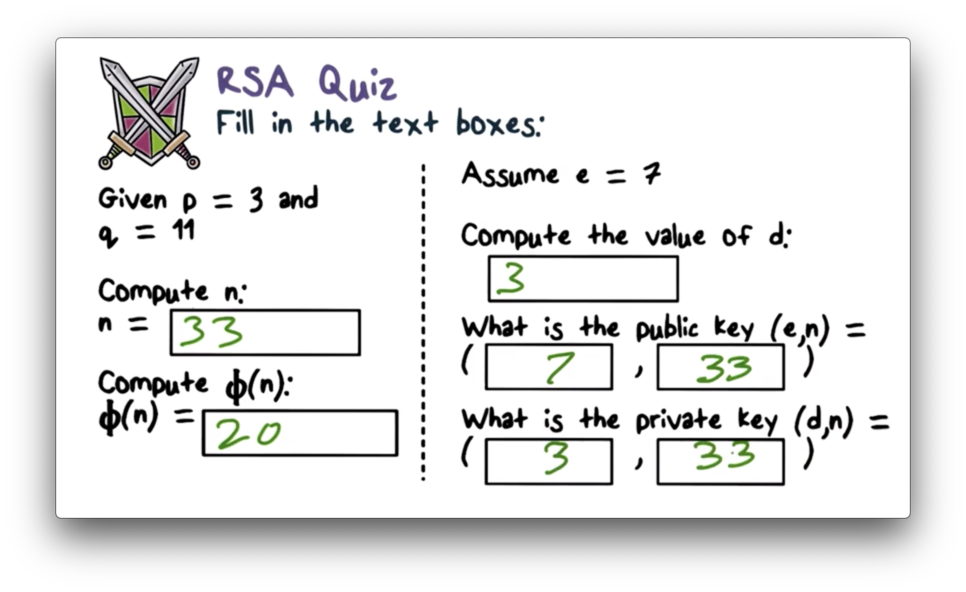
and . and must be multiplicative inverses , so for , , since . Finally, public key is equal to , and private key, is equal to .
RSA Encryption Quiz

RSA Encryption Quiz Solution

Encrypting message involves computing , which is equivalent to . Decrypting ciphertext involves computing , which is equivalent to .
RSA in Practice Quiz

RSA in Practice Quiz Solution

Always use standard libraries, as they have been reviewed and tested by experts in the field.
Diffie-Hellman Quiz
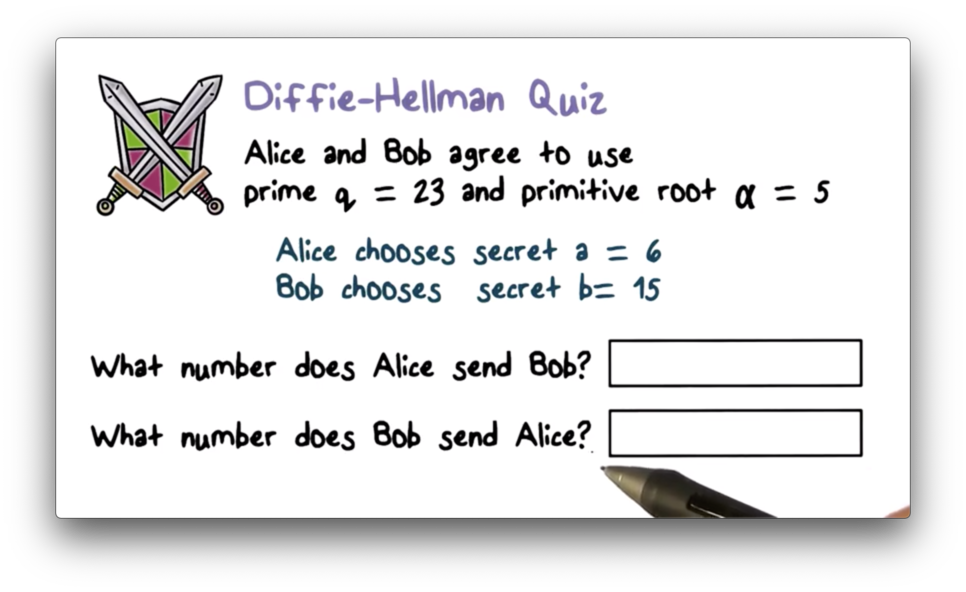
Diffie-Hellman Quiz Solution

Alice sends to Bob, which is equivalent to . Bob sends to Alice, which is equivalent to .
RSA, Diffie-Hellman Quiz

RSA, Diffie-Hellman Quiz Solution

Hashes
Hash Size Quiz
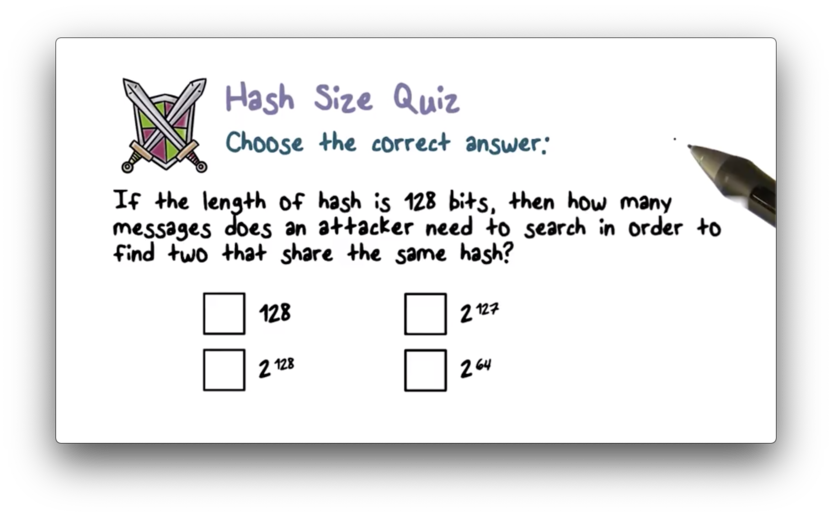
Hash Size Quiz Solution
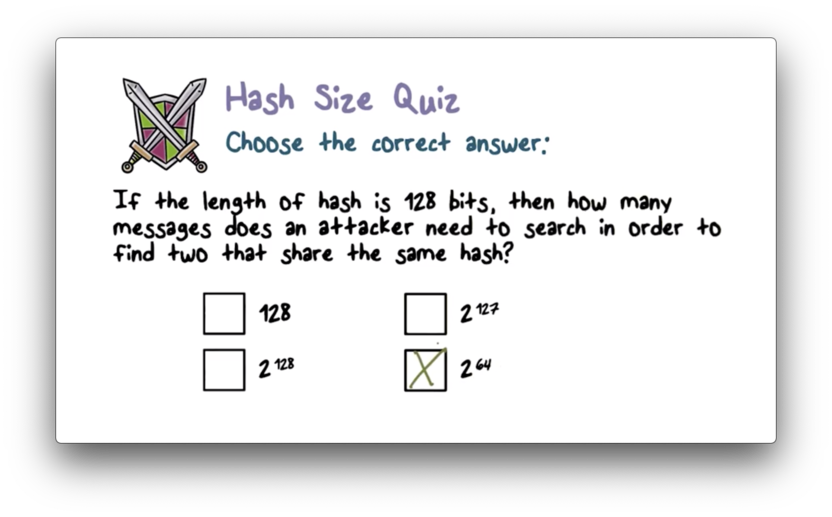
Given a hash length , an attacker needs to hash messages to find a collision. For , an attacker needs to compute hashes.
Hash Function Quiz

Hash Function Quiz Solution

Security Protocols
Mutual Authentication Quiz

Mutual Authentication Quiz Solution

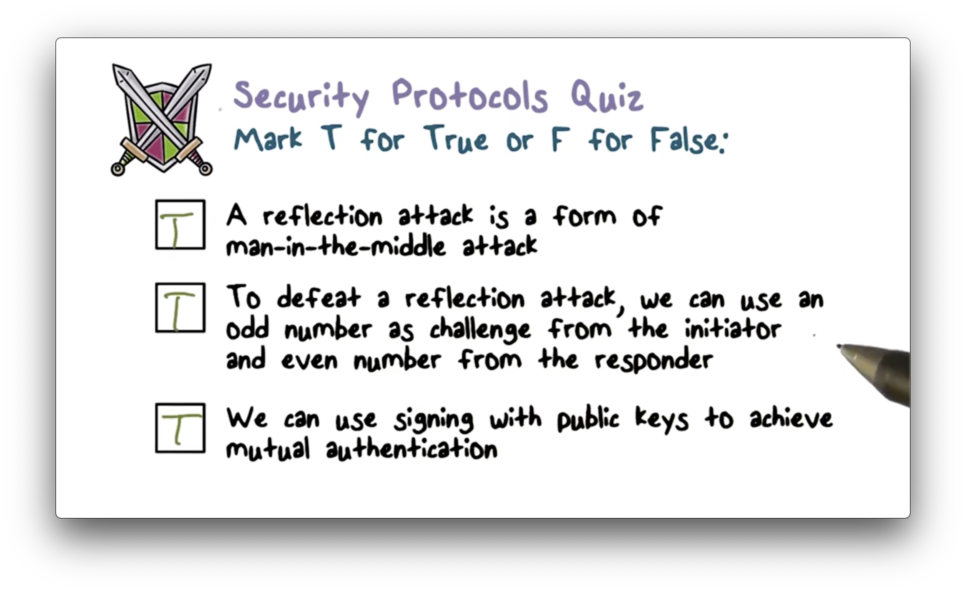
Security Protocols Quiz
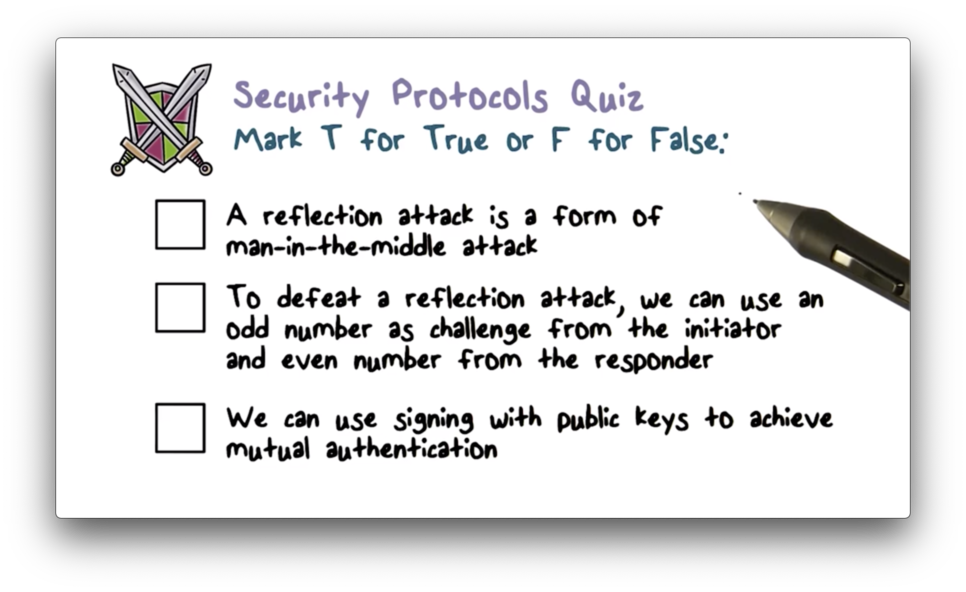
Security Protocols Quiz Solution
Session Key Quiz

Session Key Quiz Solution

Kerberos Quiz

Kerberos Quiz Solution

IPSec and TLS
Spoofing Quiz

Spoofing Quiz Solution

If you spoof your IP address, responses to your packets will not reach you. Therefore, IP spoofing is only useful for unidirectional communication.
IPSec Quiz

IPSec Quiz Solution

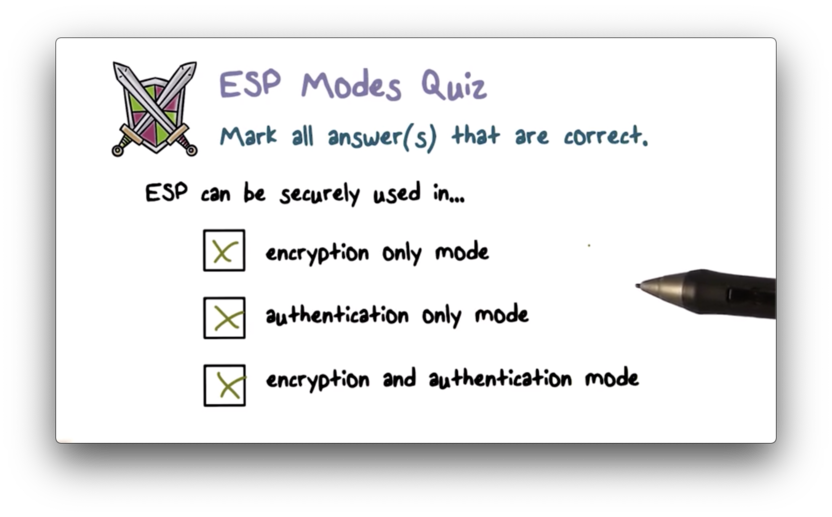
ESP Modes Quiz

ESP Modes Quiz Solution
ESP and AH Quiz

ESP and AH Quiz Solution

IPSec Quiz

IPSec Quiz Solution

Diffie Hellman Quiz

Diffie Hellman Quiz Solution

IKE Quiz

IKE Quiz Solution

TLS and SSL Quiz

TLS and SSL Quiz Solution

While transport layer protocols do rely on the IP layer, TLS does not specifically rely on IPSec.
Wireless and Mobile Security
Wifi Quiz
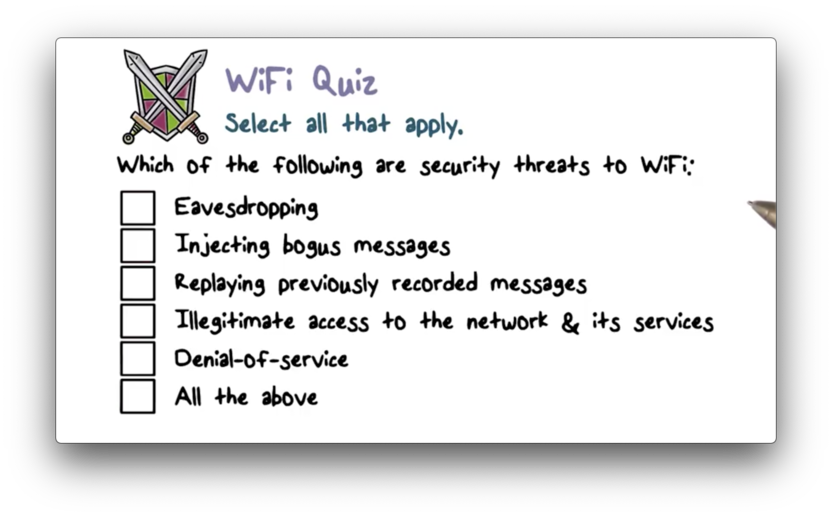
Wifi Quiz Solution

Wifi Security Standards Quiz

Wifi Security Standards Quiz Solution

Operating System Vulnerabilities Quiz
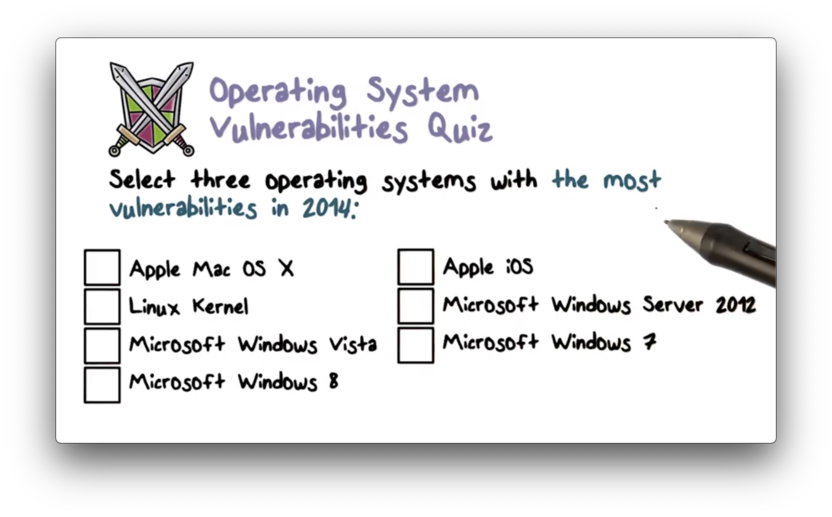
Operating System Vulnerabilities Quiz Solution
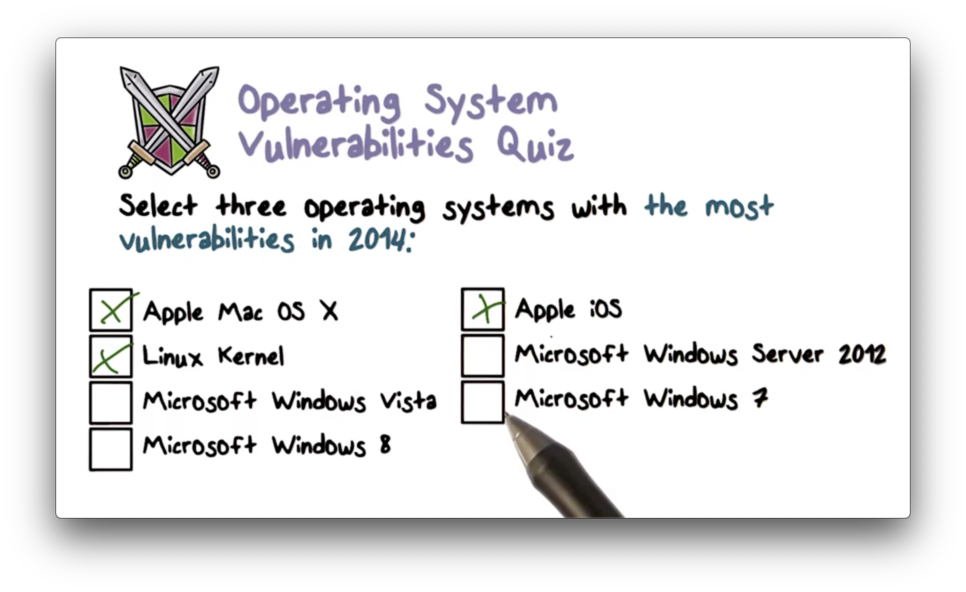
Betcha thought it was gonna be all Microsoft, didn't you? Read more here.
Security Quiz

Security Quiz Solution

App Store Security Quiz
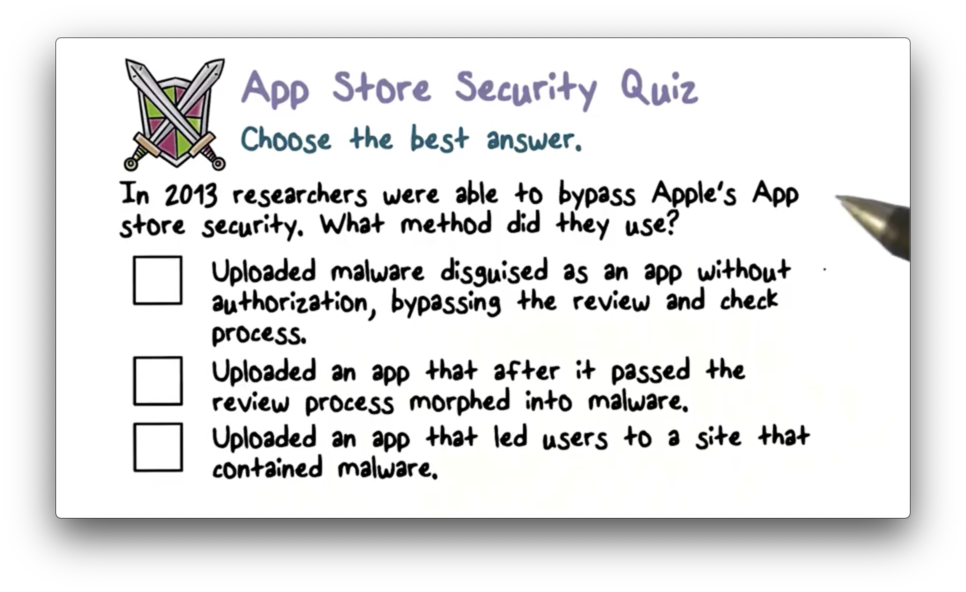
App Store Security Quiz Solution
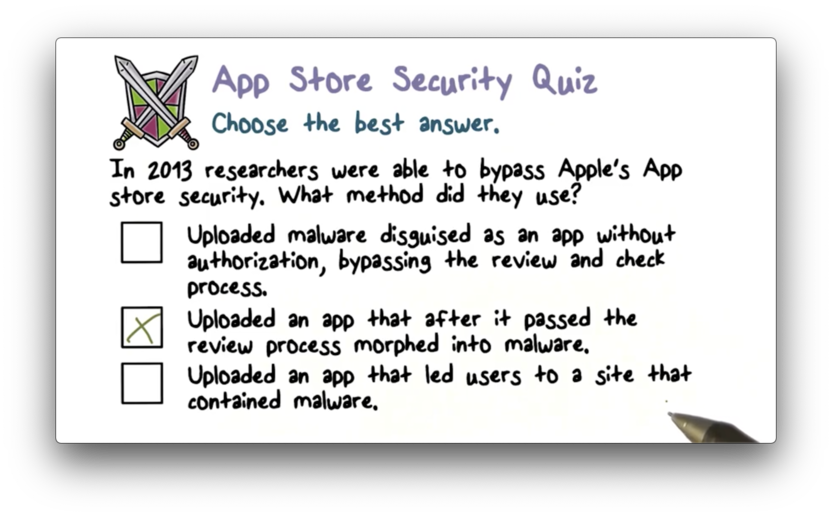
Read more here.
iOS Security Quiz
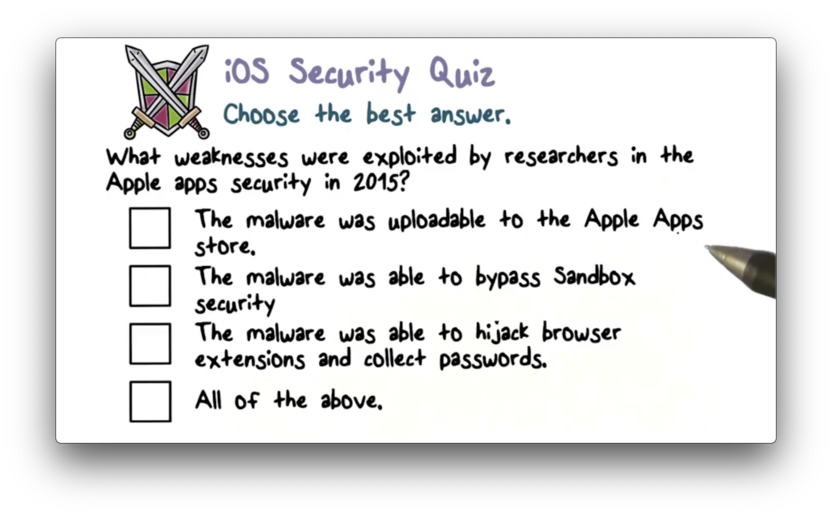
iOS Security Quiz Solution

Read more here.
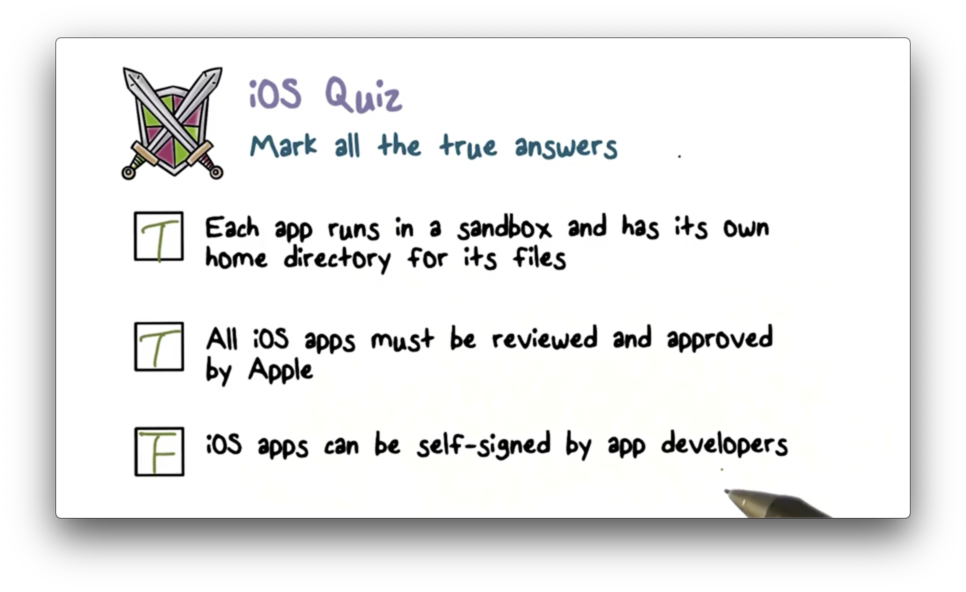
iOS Quiz
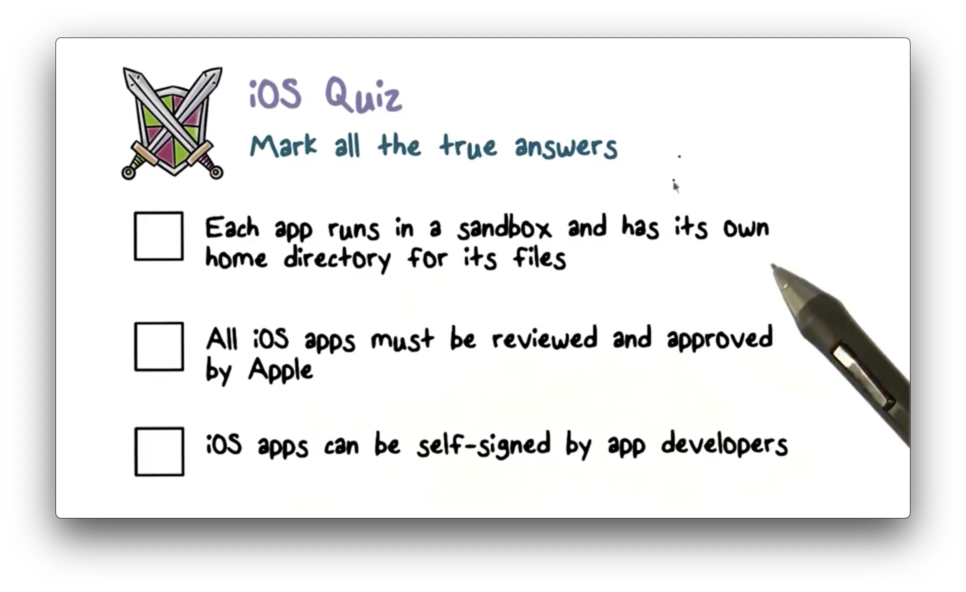
iOS Quiz Solution
Android Apps Quiz

Android Apps Quiz Solution

Web Security
Cookie Quiz
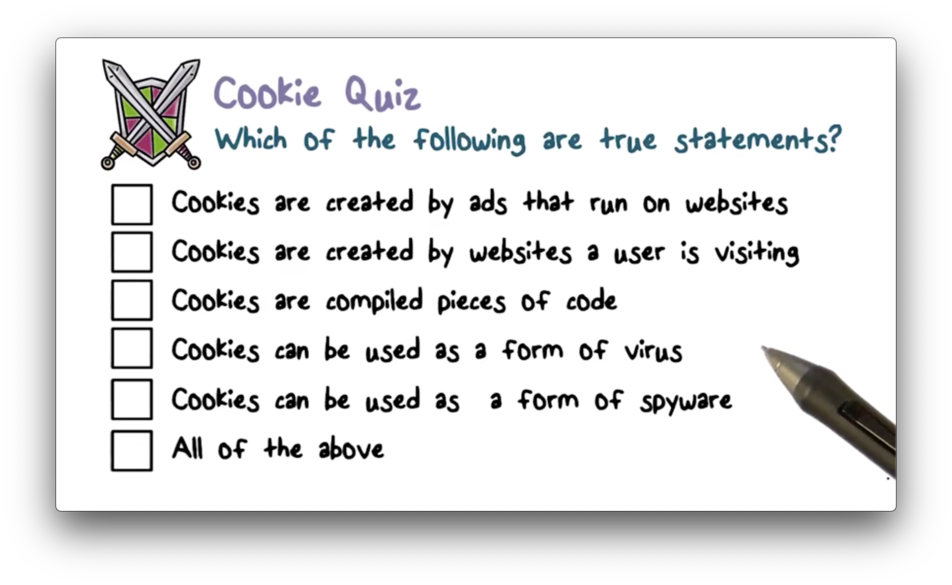
Cookie Quiz Solution
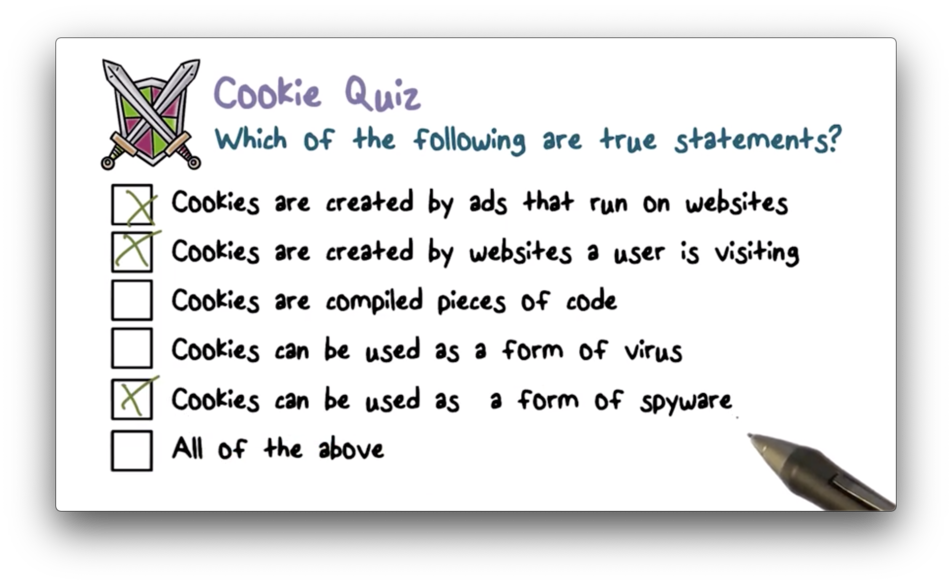
Cookies are just strings of text. They are not compiled code, and therefore cannot infect a system the way a virus can.
Web Security Quiz

Web Security Quiz Solution

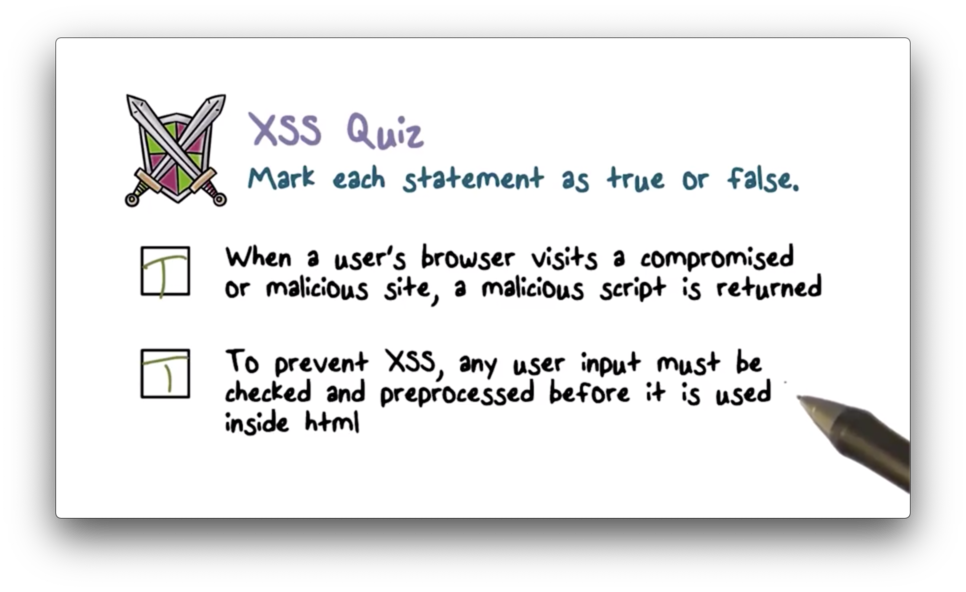
XSS Quiz
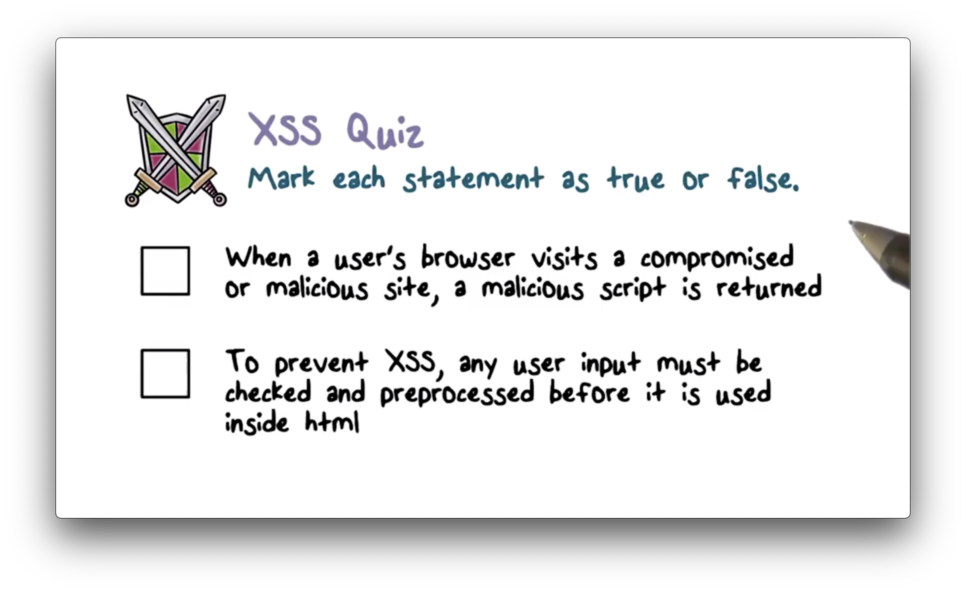
XSS Quiz Solution
XSRF Quiz

XSRF Quiz Solution

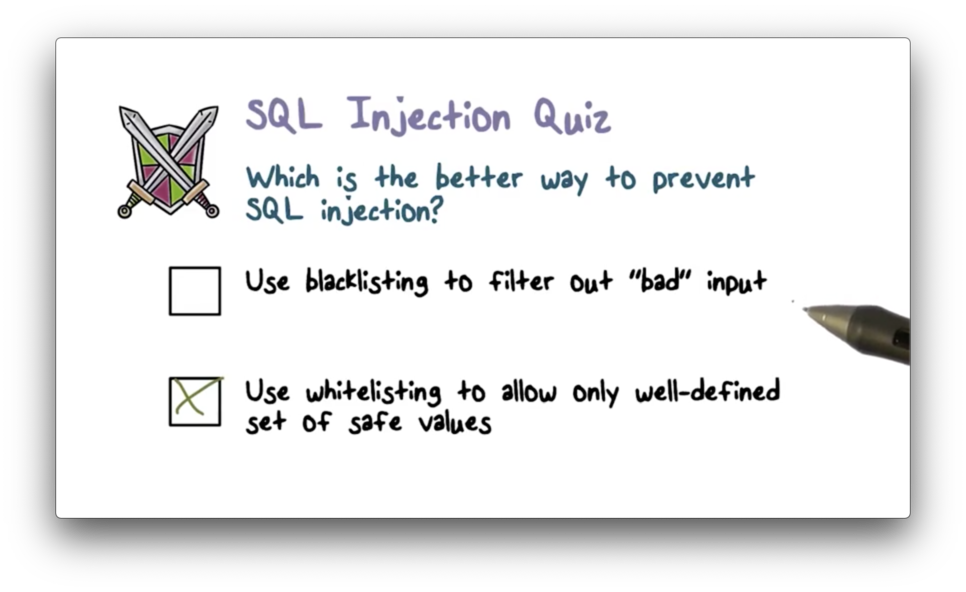
SQL Injection Quiz
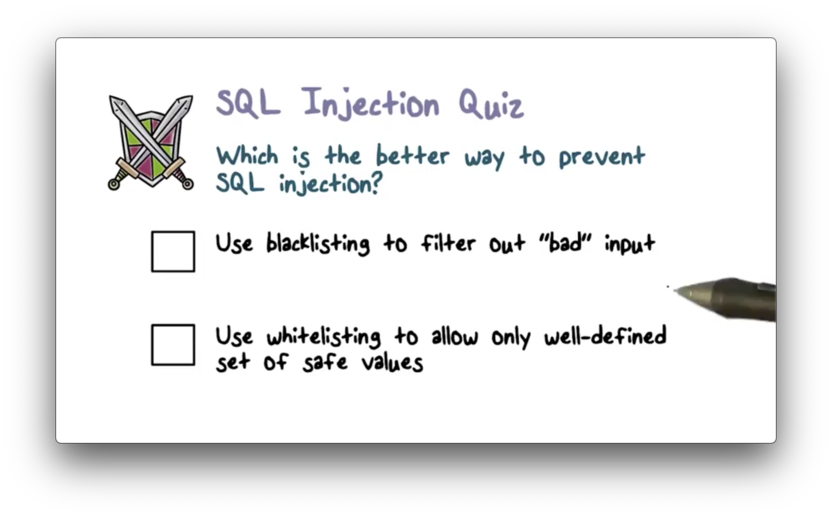
SQL Injection Quiz Solution
Cyber Security
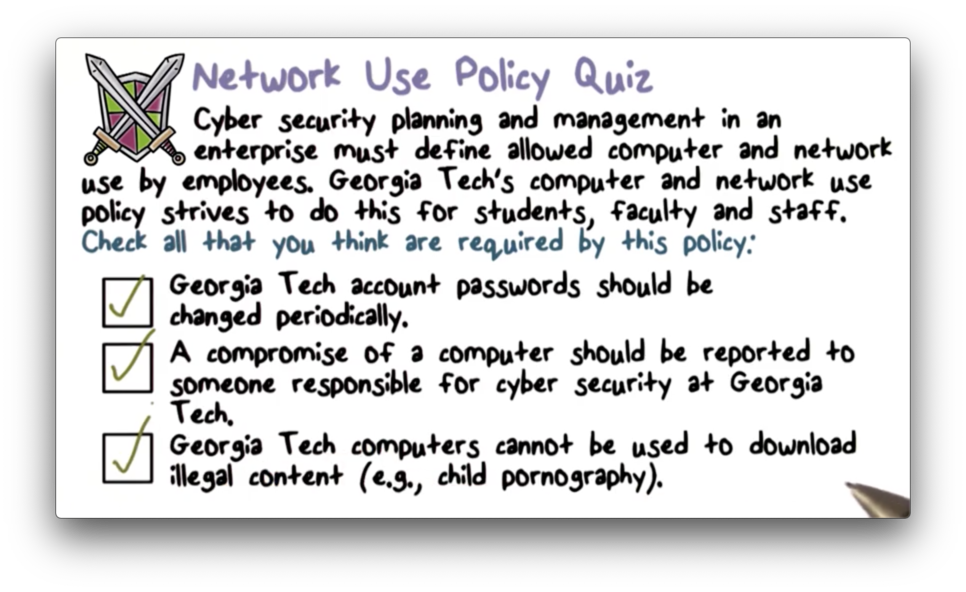
Network Use Policy Quiz

Network Use Policy Quiz Solution
Botnet Quiz

Botnet Quiz Solution

Security Audit Quiz

Security Audit Quiz Solution

NOTE: answers 1 and 3 are correct.
CISO Quiz

CISO Quiz Solution

Computer Use Policy Quiz

Computer Use Policy Quiz Solution

Student Privacy Quiz
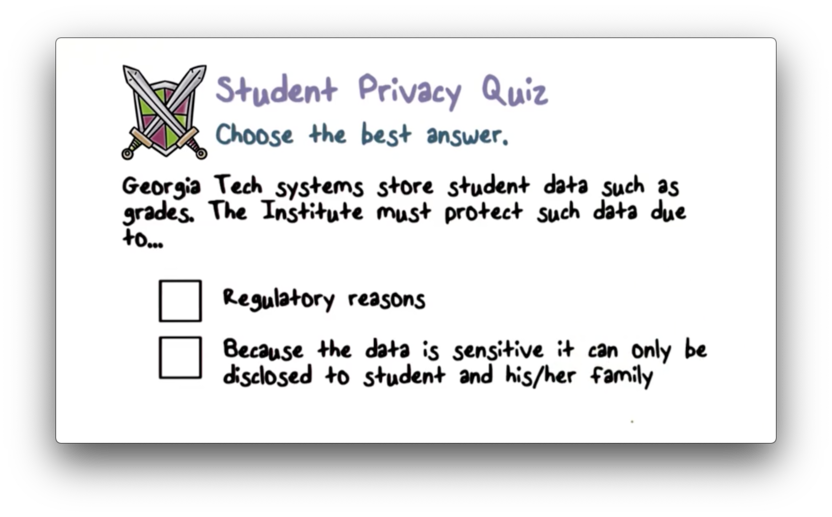
Student Privacy Quiz Solution

Anthem Breach Quiz

Anthem Breach Quiz Solution

Security Breach Quiz

Security Breach Quiz Solution

Reducing Exposure Quiz

Reducing Exposure Quiz Solution

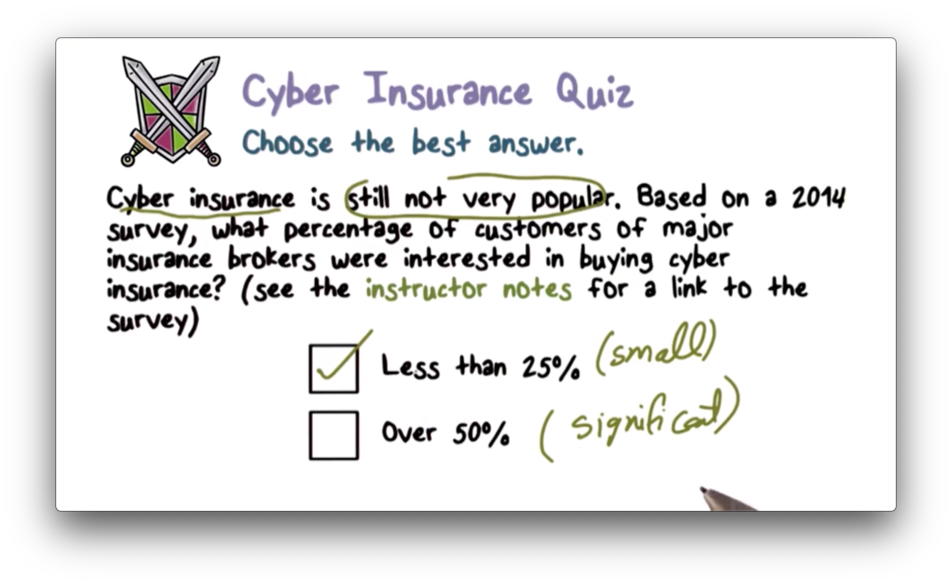
Cyber Insurance Quiz

Cyber Insurance Quiz Solution
Cyber Security Budgets Quiz

Cyber Security Budgets Quiz Solution

Read more here.
Proactive Security Quiz

Proactive Security Quiz Solution

Law, Ethics, and Privacy
Legal Deterrents Quiz

Legal Deterrents Quiz Solution

Cost of Cybercrime Quiz

Cost of Cybercrime Quiz Solution

Melissa Virus Quiz

Melissa Virus Quiz Solution

Unauthorized Access Quiz

Unauthorized Access Quiz Solution

DMCA Exclusions Quiz

DMCA Exclusions Quiz Solution

Computer Ethics Quiz

Computer Ethics Quiz Solution

Responsible Disclosure Quiz

Responsible Disclosure Quiz Solution

Privacy Quiz

Privacy Quiz Solution

Read more here.
Right to Be Forgotten Quiz

Right to Be Forgotten Quiz Solution

EFF Quiz

EFF Quiz Solution

Read more here
Google Privacy Policy Quiz

Google Privacy Policy Quiz Solution

Legal Deterrents Quiz

Legal Deterrents Quiz Solution

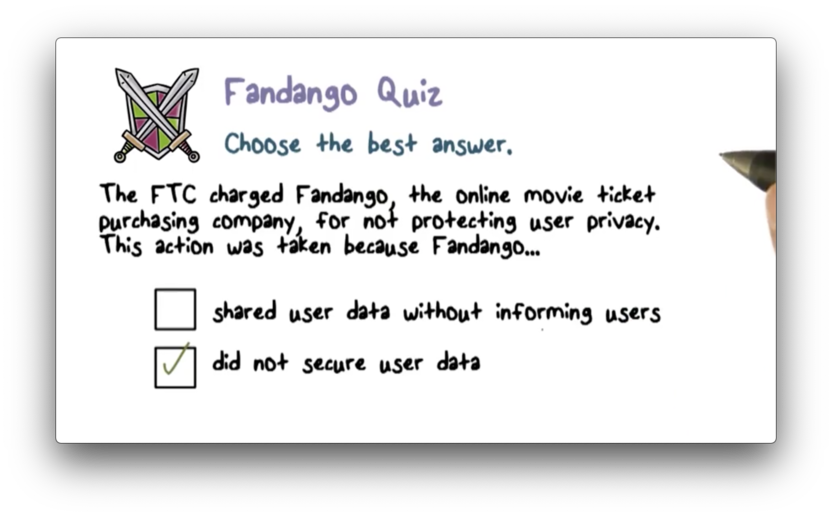
Fandango Quiz
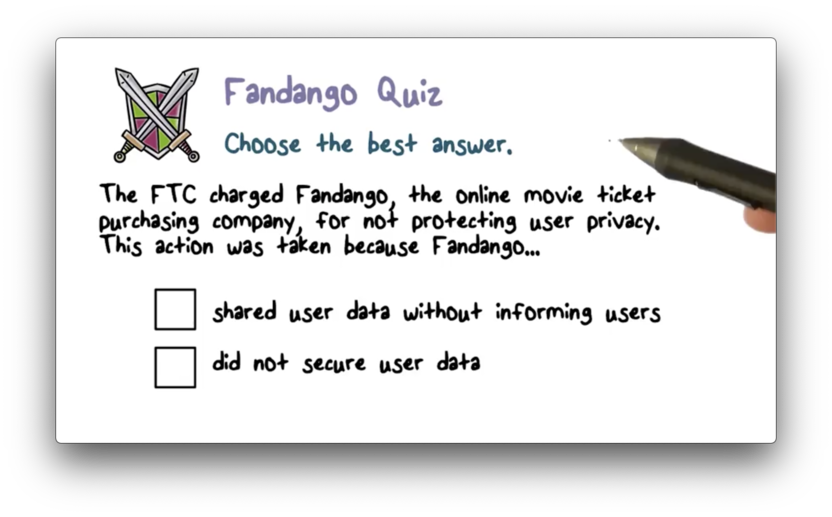
Fandango Quiz Solution
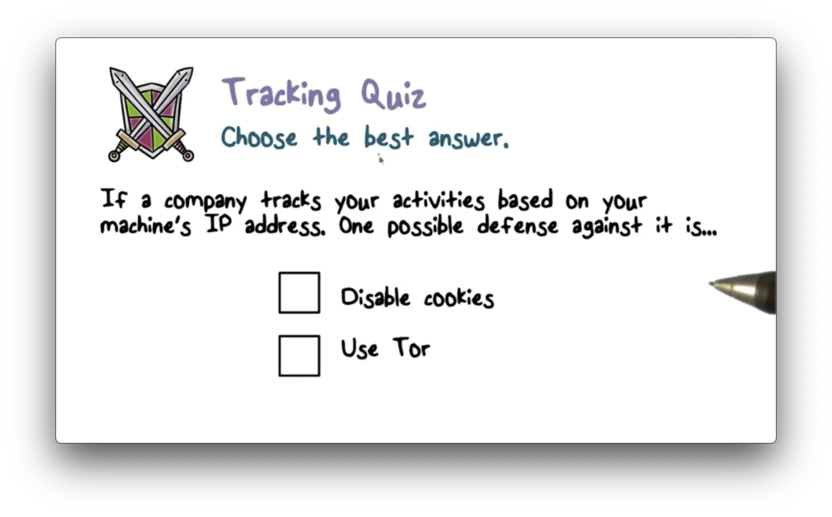
Tracking Quiz
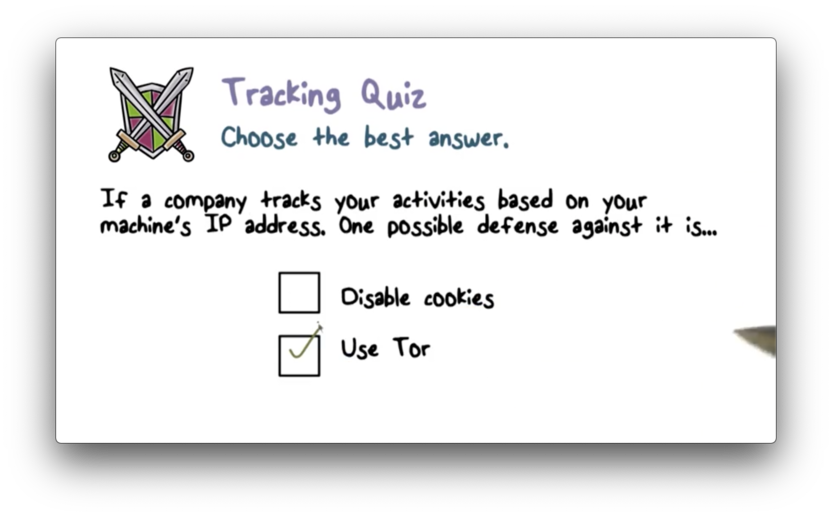
Tracking Quiz Solution
OMSCS Notes is made with in NYC by Matt Schlenker.
Copyright © 2019-2023. All rights reserved.
privacy policy